Oski
اللَّهُمَّ إِنِّي أَسْأَلُكَ عِلْمًا نَافِعًا، وَرِزْقًا طَيِّبًا، وَعَمَلًا مُتَقَبَّلًا
Date: 10/10/2025
By: Y0un15
Labs’s link: Oski – CyberDefenders
1-Scenario
The accountant at the company received an email titled “Urgent New Order” from a client late in the afternoon. When he attempted to access the attached invoice, he discovered it contained false order information. Subsequently, the SIEM solution generated an alert regarding downloading a potentially malicious file. Upon initial investigation, it was found that the PPT file might be responsible for this download. Could you please conduct a detailed examination of this file?
2. Pre Investigation
We are givven with this MD5 Hash: 12c1842c3ccafe7408c23ebf292ee3d9
That what yeild after searching with it one virustotal
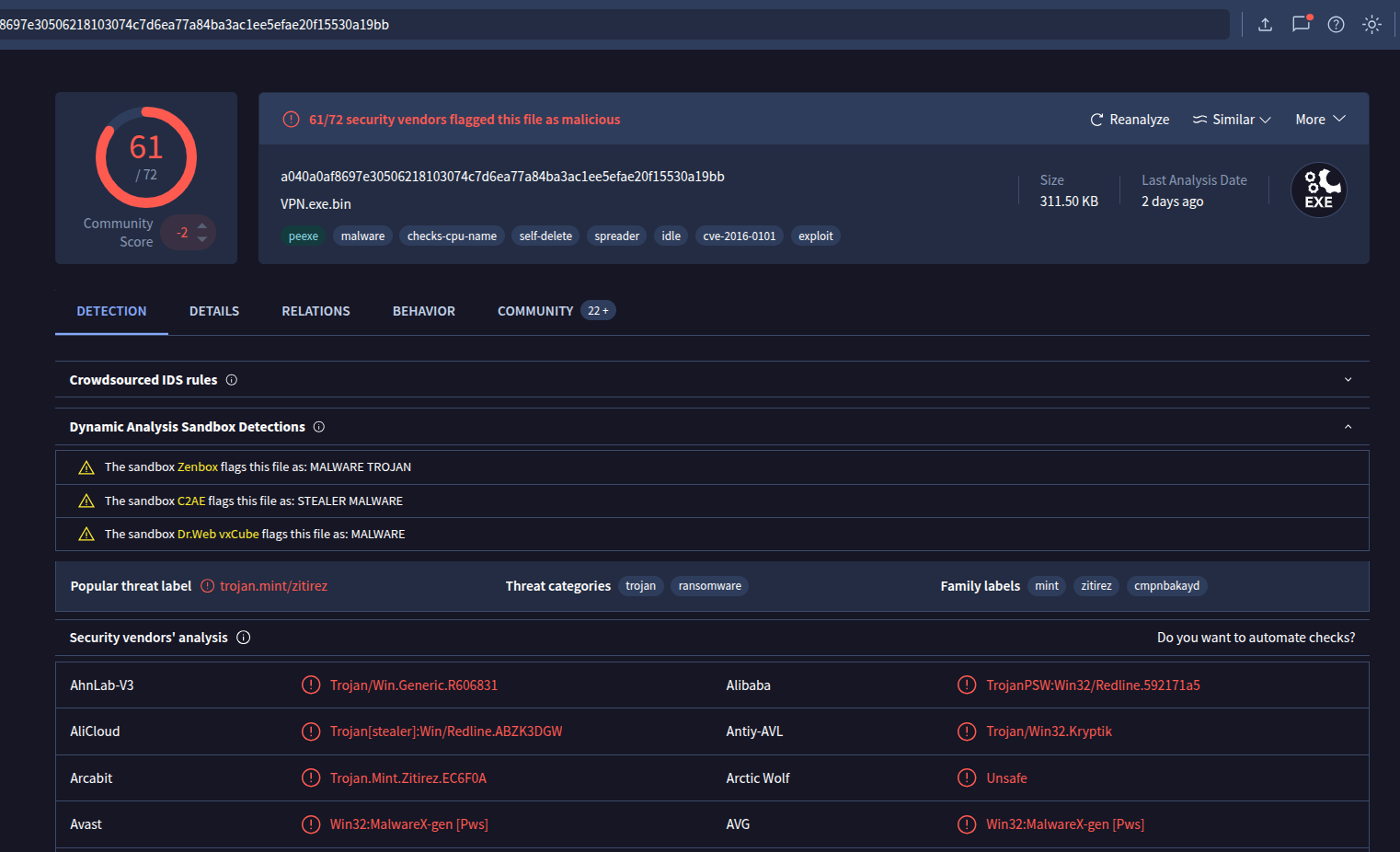 so lets go to see the question.
so lets go to see the question.
3. Challenge Questions
🔹Determining the creation time of the malware can provide insights into its origin. What was the time of malware creation?
🔹Identifying the command and control (C2) server that the malware communicates with can help trace back to the attacker. Which C2 server does the malware in the PPT file communicate with?
🔹Identifying the initial actions of the malware post-infection can provide insights into its primary objectives. What is the first library that the malware requests post-infection?
🔹By examining the provided Any.run report, what RC4 key is used by the malware to decrypt its base64-encoded string?
🔹By examining the MITRE ATT&CK techniques displayed in the Any.run sandbox report, identify the main MITRE technique (not sub-techniques) the malware uses to steal the user’s password.
🔹By examining the child processes displayed in the Any.run sandbox report, which directory does the malware target for the deletion of all DLL files?
🔹Understanding the malware’s behavior post-data exfiltration can give insights into its evasion techniques. By analyzing the child processes, after successfully exfiltrating the user’s data, how many seconds does it take for the malware to self-delete?
4-Walking through the Questions
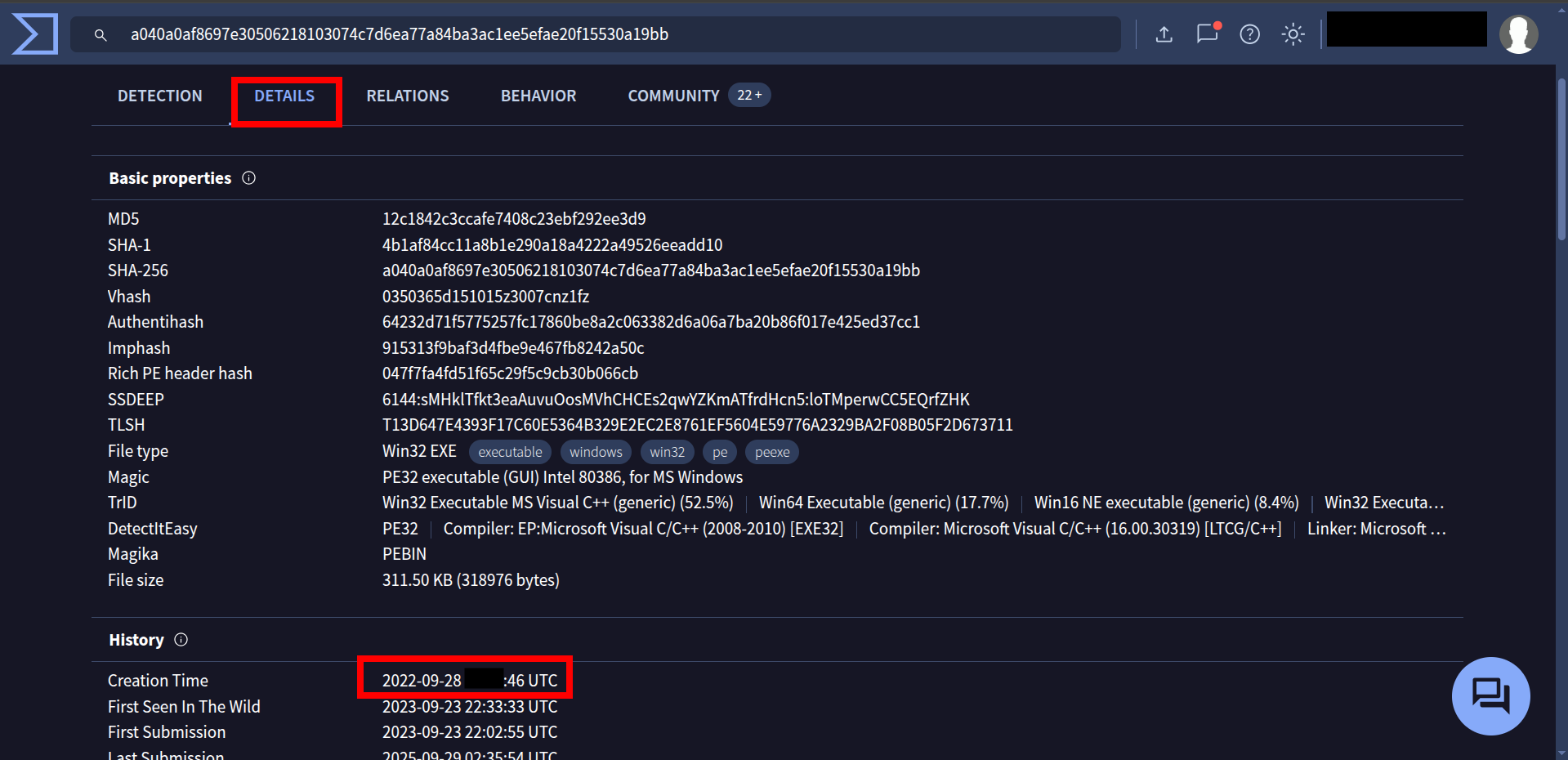
🔹 Q1 — creation time
Going to Details section on virustotal you will see the creation time and some other info about this malware’s History
🔹 Q2 — C2 server
Going to Behaviour section on virustotal shows a file’s actions after being executed in a controlled sandbox environment and at the Http requestes you can get the answer for this question.
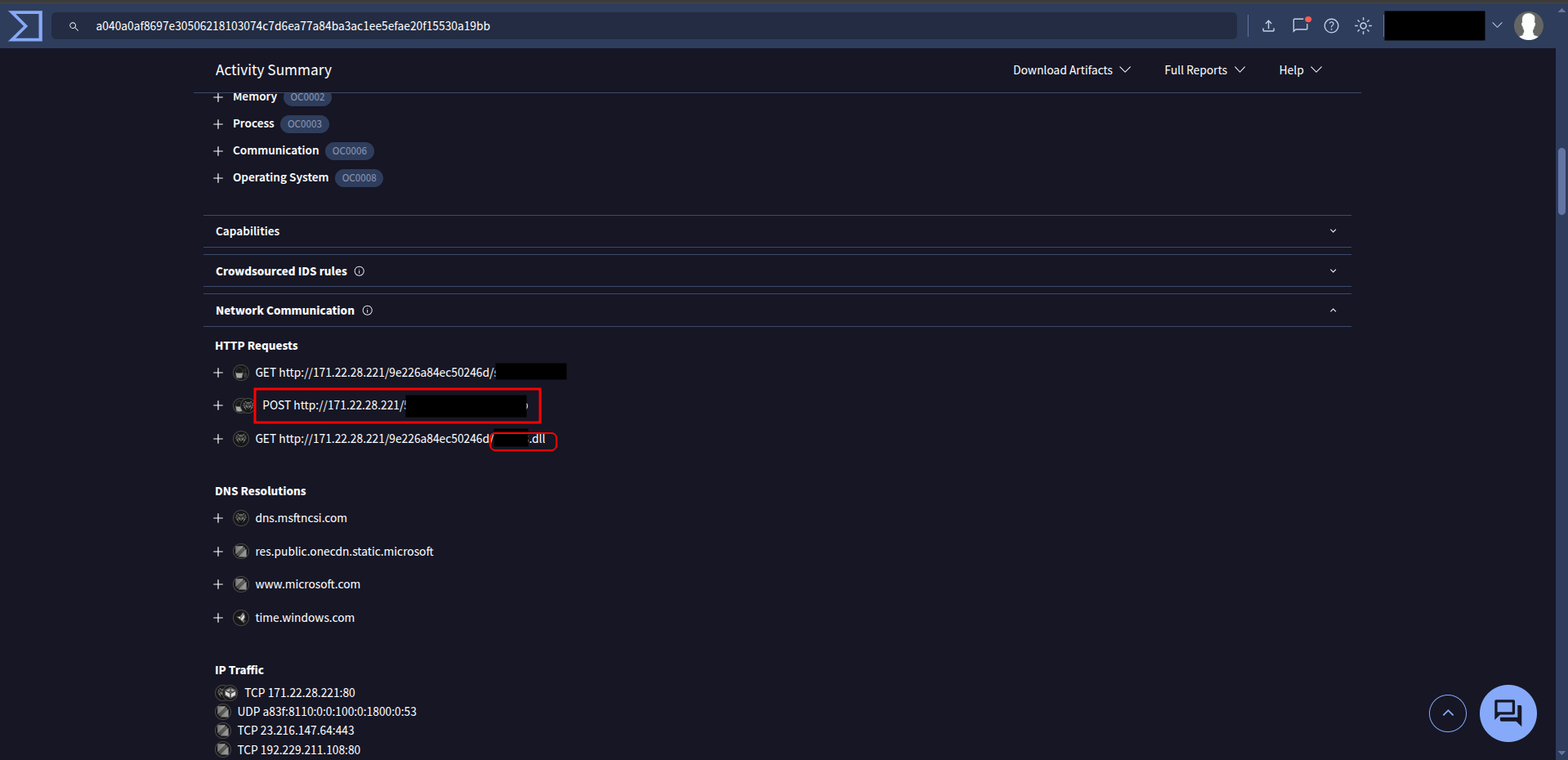
🔹 Q3 — What is the first library that the malware requests post-infection?
On the Http requestes and the GET request you will see the first libriry that get infected

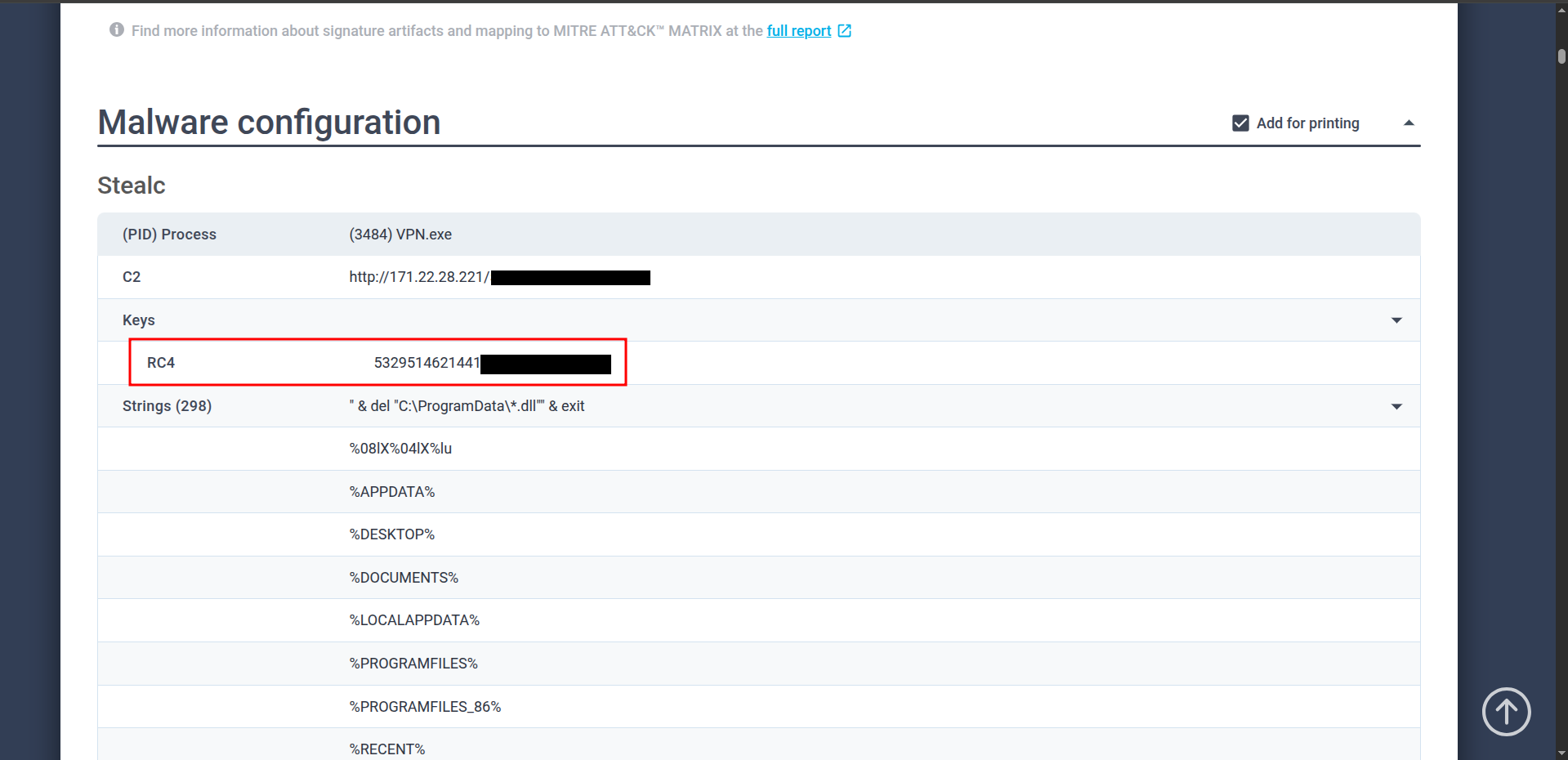
🔹 Q4 — RC4 key
Follwing the report link then to Malware configuration section you will see the keys ,C2 adn strings also the PID
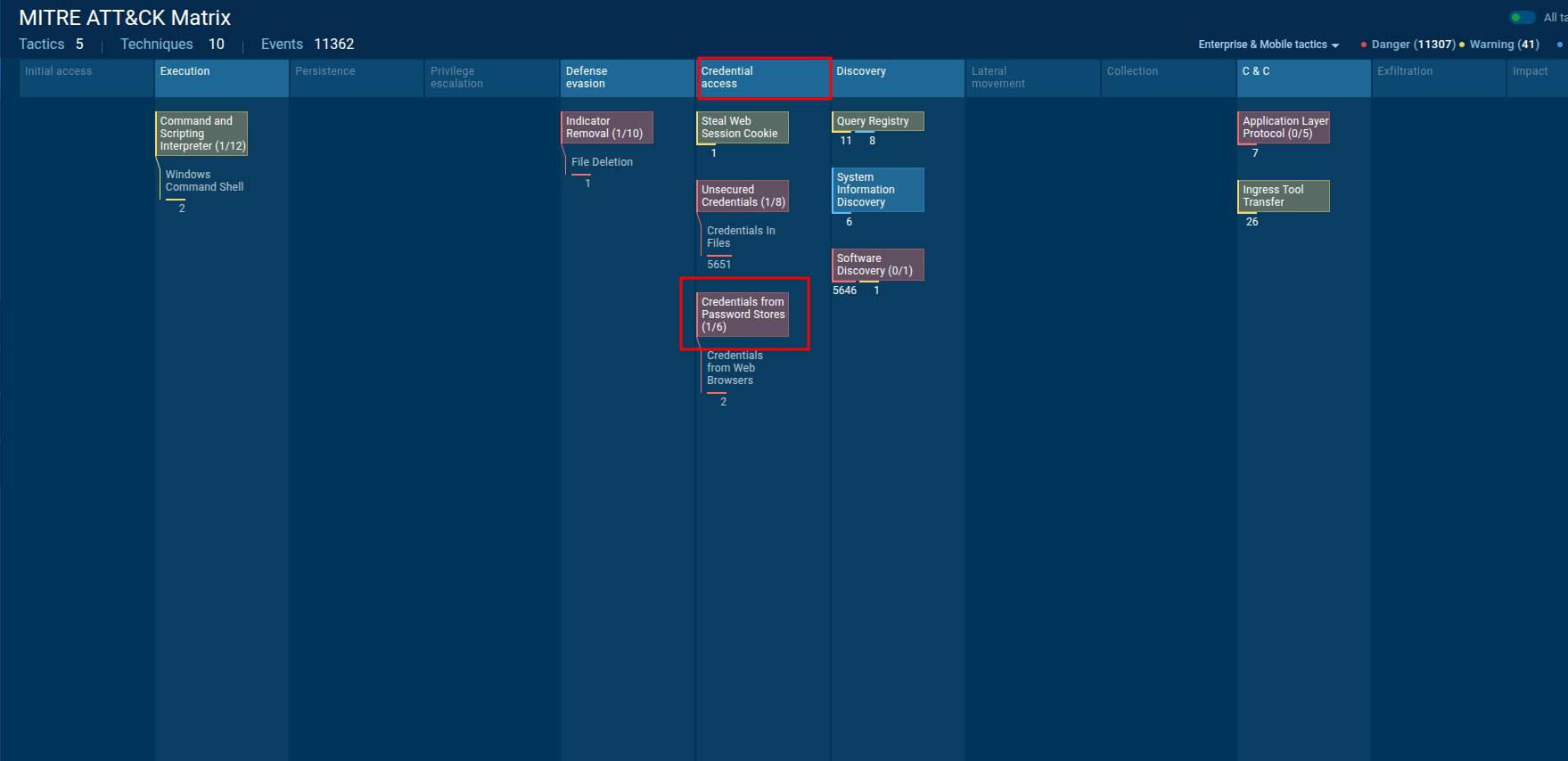
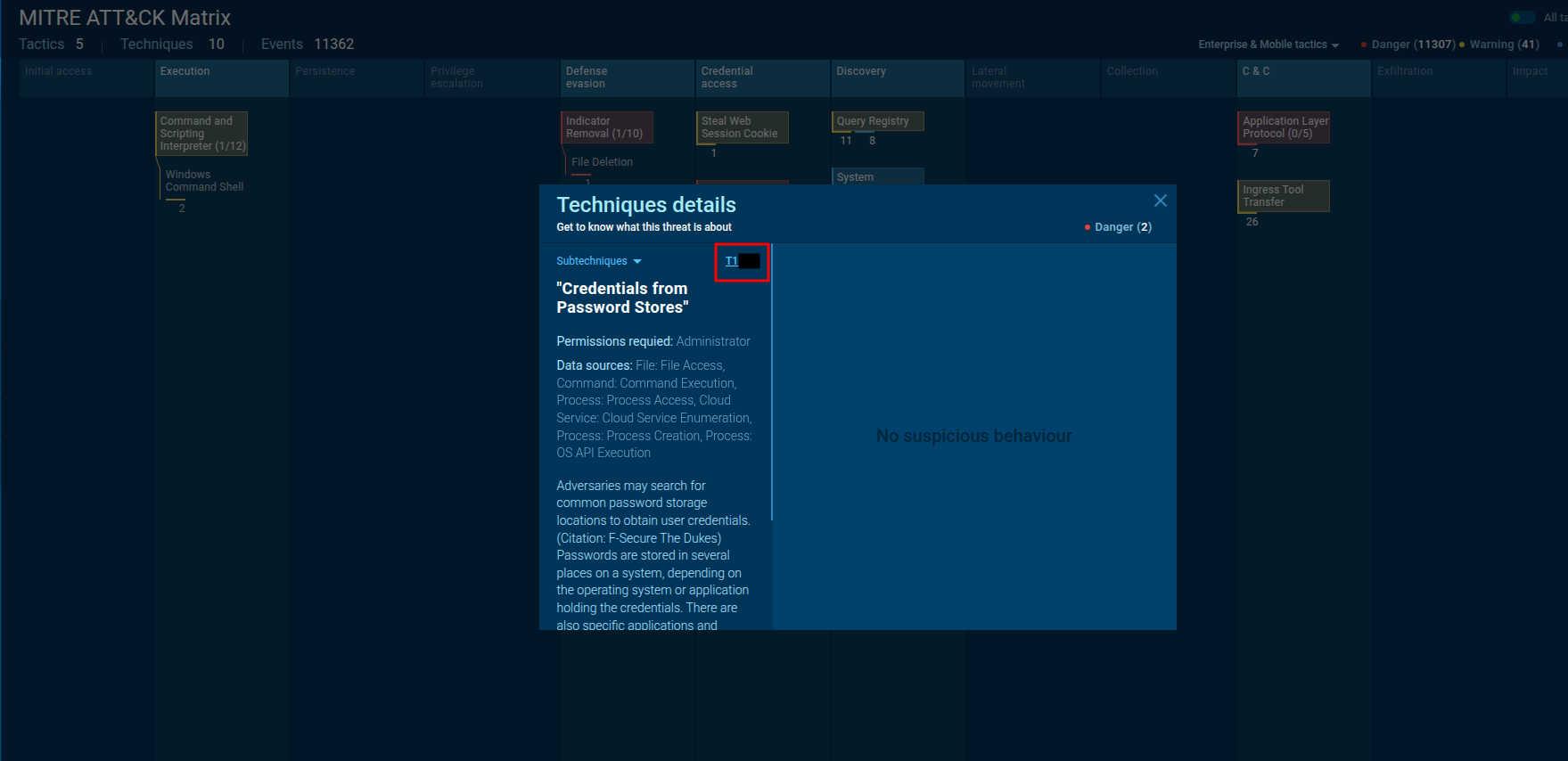
🔹 Q5 — MITRE technique the malware uses to steal the user’s password
Follwing the report link then to ATT&CK
🔹 Q6 — which directory does the malware target for the deletion of all DLL files?
From the child processes listed in the Any.run report then to the cmde.exe you will see the commmand that the malware performed
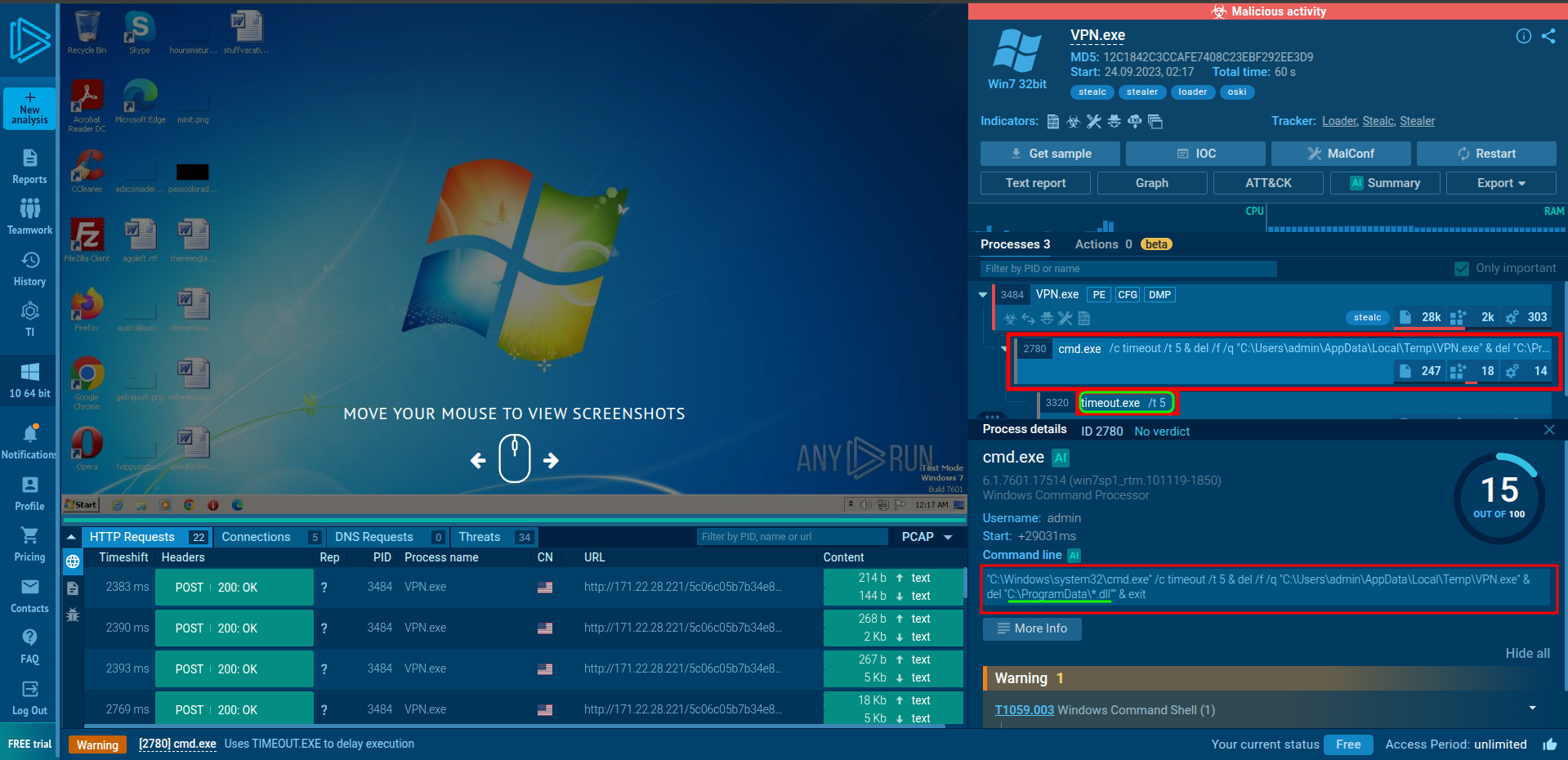
🔹 Q7 — , how many seconds does it take for the malware to self-delete?
"C:\Windows\system32\cmd.exe" /c timeout /t 5 & del /f /q "C:\Users\admin\AppData\Local\Temp\VPN.exe" & del "C:\ProgramData\*.dll"" & exit
 so the answer is 5
so the answer is 5
And that’s all for today’s write-up!
I hope you enjoyed it — see you in the next one! 👋🏻
اللهم انفعنا بما علَّمتنا، وعلِّمنا ما ينفعنا، وزِدنا علمًا وفقهًا وفهمًا