Lockdown
اللَّهُمَّ إِنِّي أَسْأَلُكَ عِلْمًا نَافِعًا، وَرِزْقًا طَيِّبًا، وَعَمَلًا مُتَقَبَّلًا
Date: 11/10/2025
By: Y0un15
Labs’s link : Lockdown – CyberDefenders
1-Scenario:
TechNova Systems’ SOC has detected suspicious outbound traffic from a public-facing IIS server in its cloud platform—activity suggestive of a web-shell drop and covert connections to an unknown host.
As the forensic examiner, you have three critical artefacts in hand: a PCAP capturing the initial traffic, a full memory image of the server, and a malware sample recovered from disk. Reconstruct the intrusion and all of the attacker’s activities so TechNova can contain the breach and strengthen its defenses.
2. Pre Investigation :
I began by examining the PCAP file to identify suspicious communication patterns.
The capture contained roughly 6,359 packets. Viewing the IPv4 conversation list in Wireshark quickly highlighted an unusual amount of traffic between two hosts:
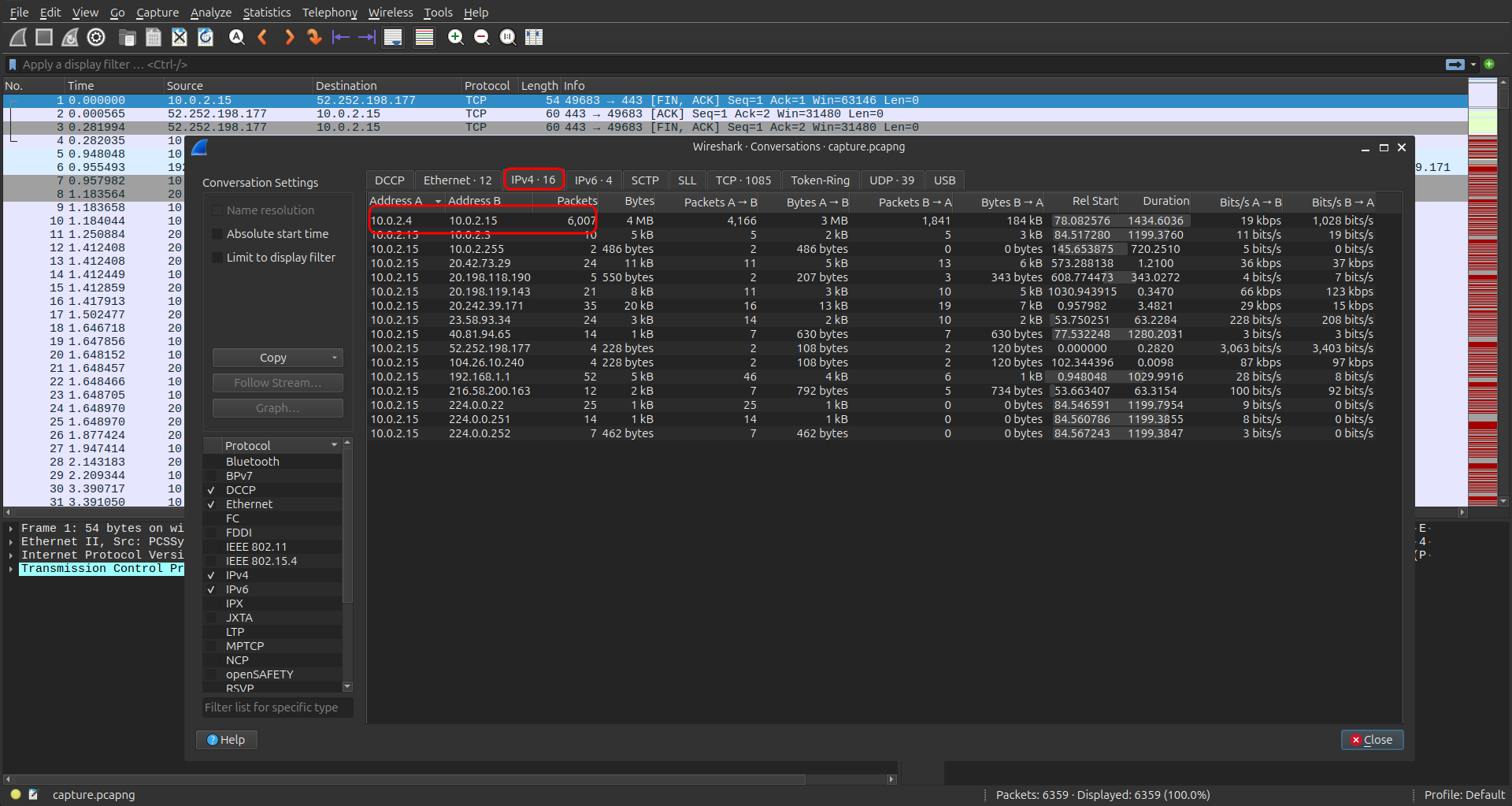
This heavy packet exchange indicated a potential reconnaissance or flooding attack, likely from the attacker’s host against the IIS server.
Protocol Behavior
Drilling deeper into the protocols, I focused on TCP streams, which confirmed the same IP pair — consistent with port enumeration or service discovery activity.
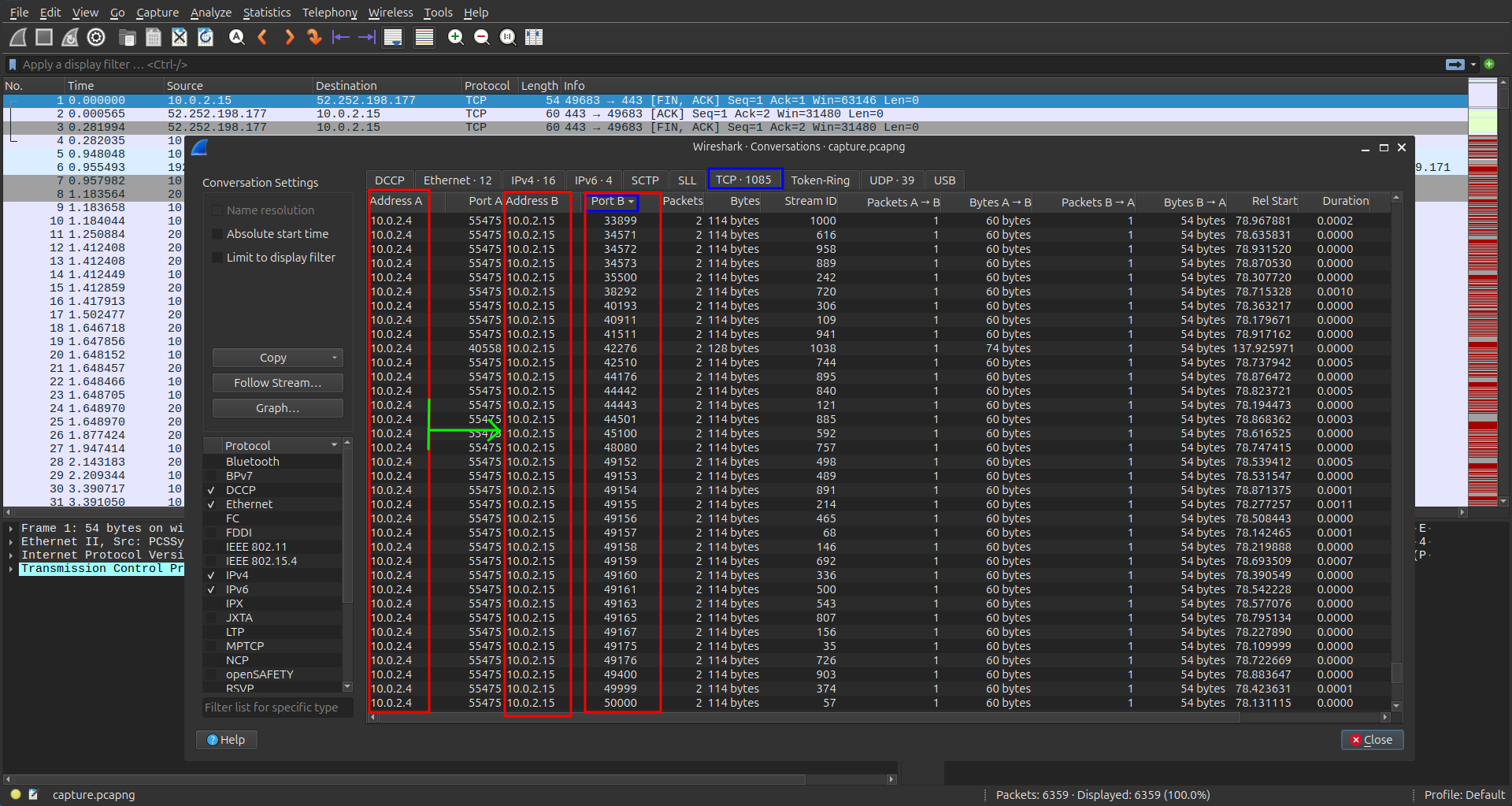 At this point, I suspected the attacker was probing for open ports to identify a weak entry point.
At this point, I suspected the attacker was probing for open ports to identify a weak entry point.
Before moving to the challenge questions, I also reviewed the malware sample (updatenow.exe) found on disk.
Malware Overview
Static inspection revealed:
- File type:
PE32 executable (GUI) Intel 80386, UPX compressed - SHA256 hash submitted to VirusTotal yielded strong detection results:
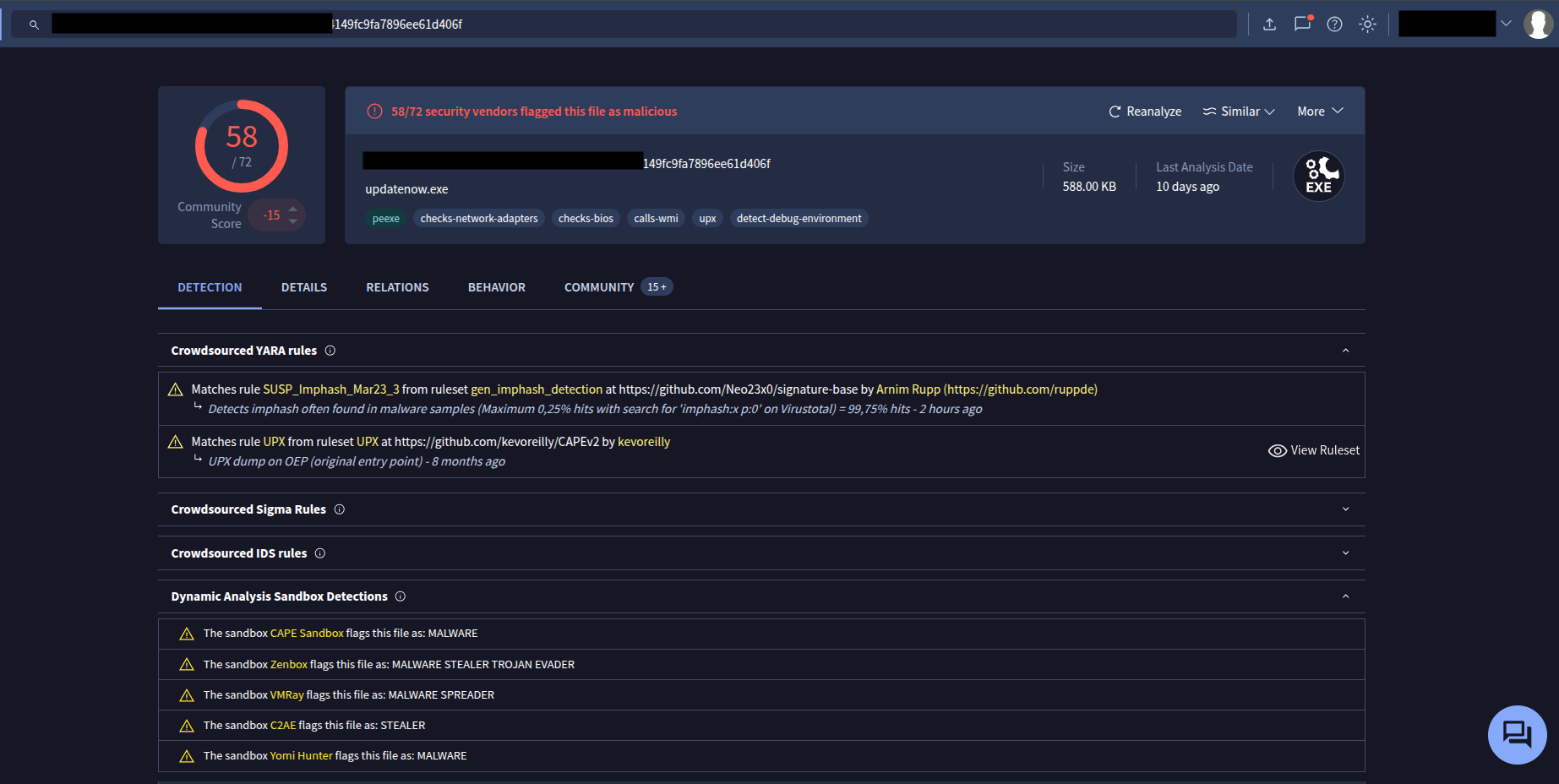
With this context, I proceeded to answer the challenge questions.
3. Challenge Questions:
PcapPCAP Analysis
🔹After flooding the IIS host with rapid-fire probes, the attacker reveals their origin. Which IP address generated this reconnaissance traffic?
🔹Zeroing in on a single open service to gain a foothold, the attacker carries out targeted enumeration. Which MITRE ATT&CK technique ID covers this activity?
🔹While reviewing the SMB traffic, you observe two consecutive Tree Connect requests that expose the first shares the intruder probes on the IIS host. Which two full UNC paths are accessed?
🔹Inside the share, the attacker plants a web-accessible payload that will grant remote code execution. What is the filename of the malicious file they uploaded, and what byte length is specified in the corresponding SMB2 Write Request?
🔹The newly planted shell calls back to the attacker over an uncommon but firewall-friendly port. Which listening port did the attacker use for the reverse shell?
Memory Dump Aanlysis
🔹Your memory snapshot captures the system’s kernel in situ, providing vital context for the breach. What is the kernel base address in the dump?
🔹A trusted service launches an unfamiliar executable residing outside the usual IIS stack, signalling a persistence implant. What is the final full on-disk path of that executable, and which MITRE ATT&CK persistence technique ID corresponds to this behaviour?
🔹The reverse shell’s outbound traffic is handled by a built-in Windows process that also spawns the implanted executable. What is the name of this process, and what PID does it run under?
Malware Sample Analysis
🔹Static inspection reveals the binary has been packed to hinder analysis. Which packer was used to obfuscate it?
🔹Threat-intel analysis shows the malware beaconing to its command-and-control host. Which fully qualified domain name (FQDN) does it contact?
🔹Open-source intel associates that hash with a well-known commodity RAT. To which malware family does the sample belong?
4-Walking through the Questions :
🔹 Q1 — Attacker’s Reconnaissance Source
As shown in the image, there is a suspicious conversation between the two IPs:

After scrolling through the conversation, that what i found
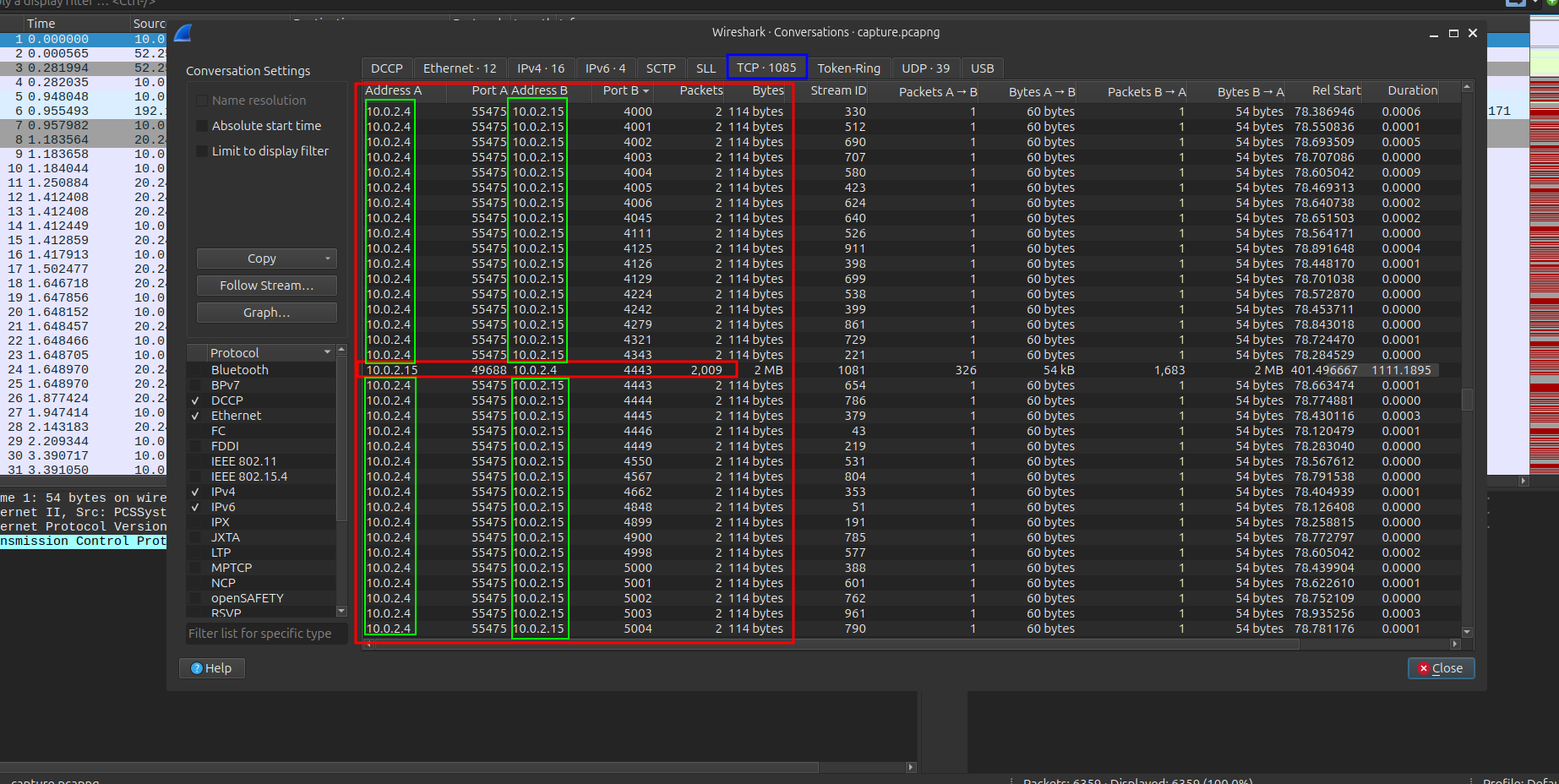
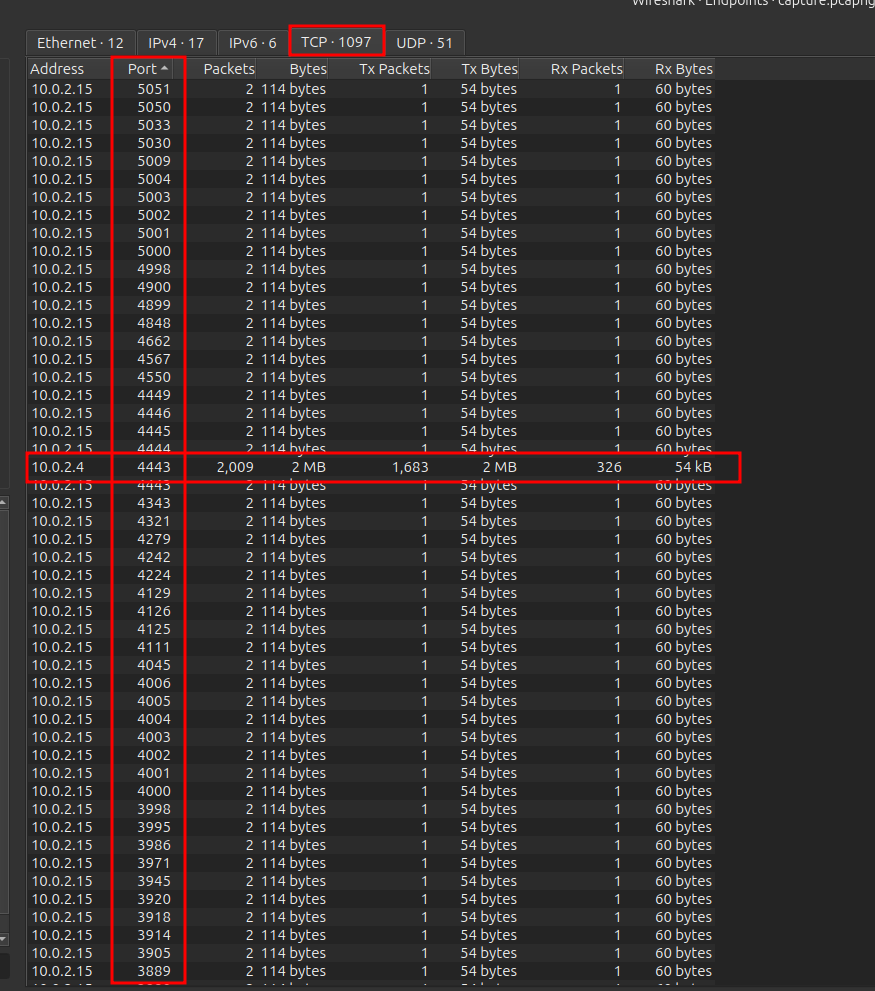
So the IP address generating this traffic is 10.0.2.4 ,and The listener port used for the reverse shell is 4443, which we will use for Q5.
🔹 Q2 — MITRE ATT&CK technique ID
The attacker performed port enumeration to discover an open service on the IIS host.By googling that i get the correct technique ID.
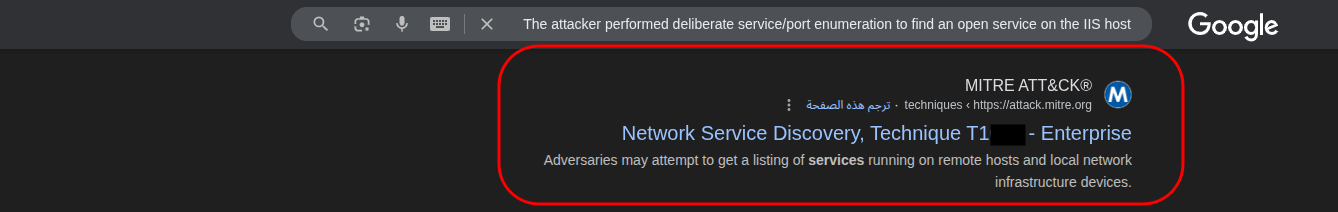
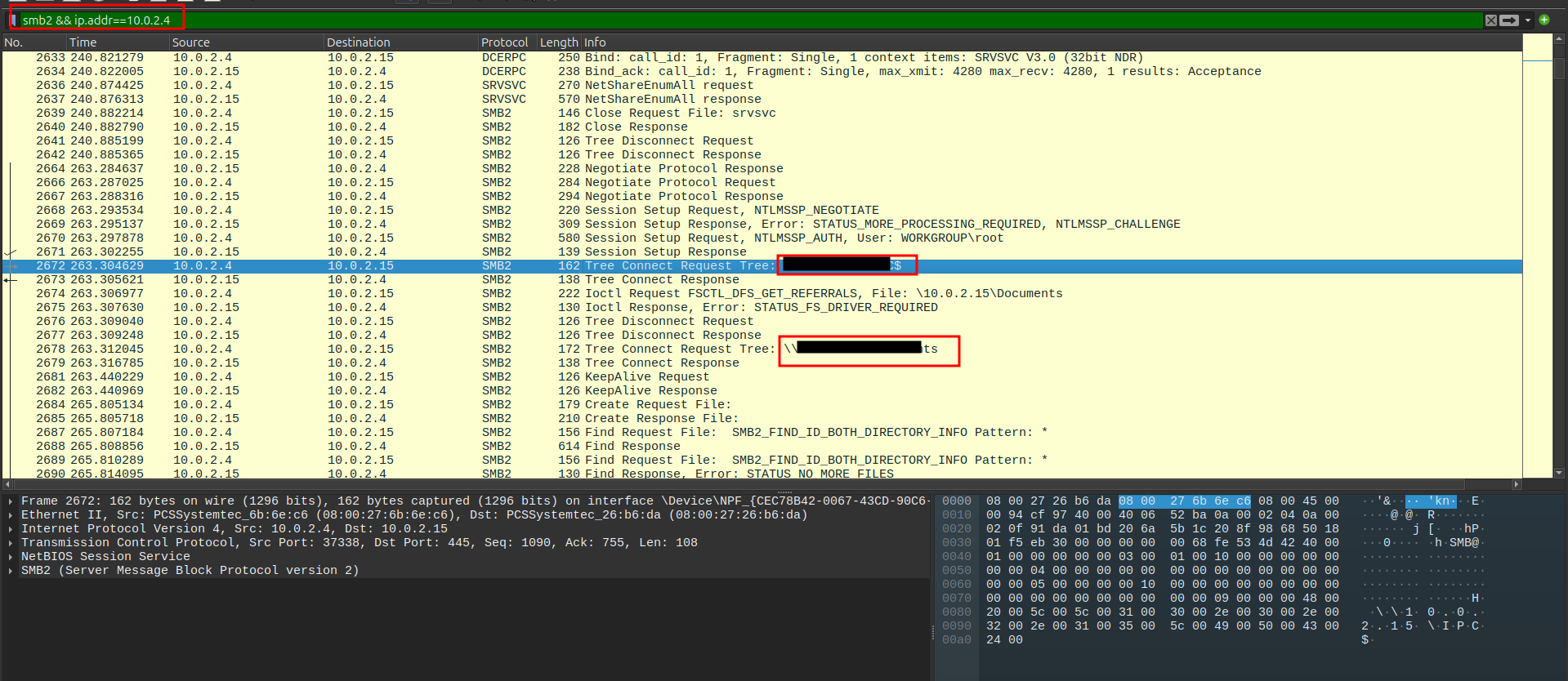
🔹 Q3 — Which two full UNC paths are accessed?
Applying an SMB2 filter together with the attacker reveal the full UNC pathes .
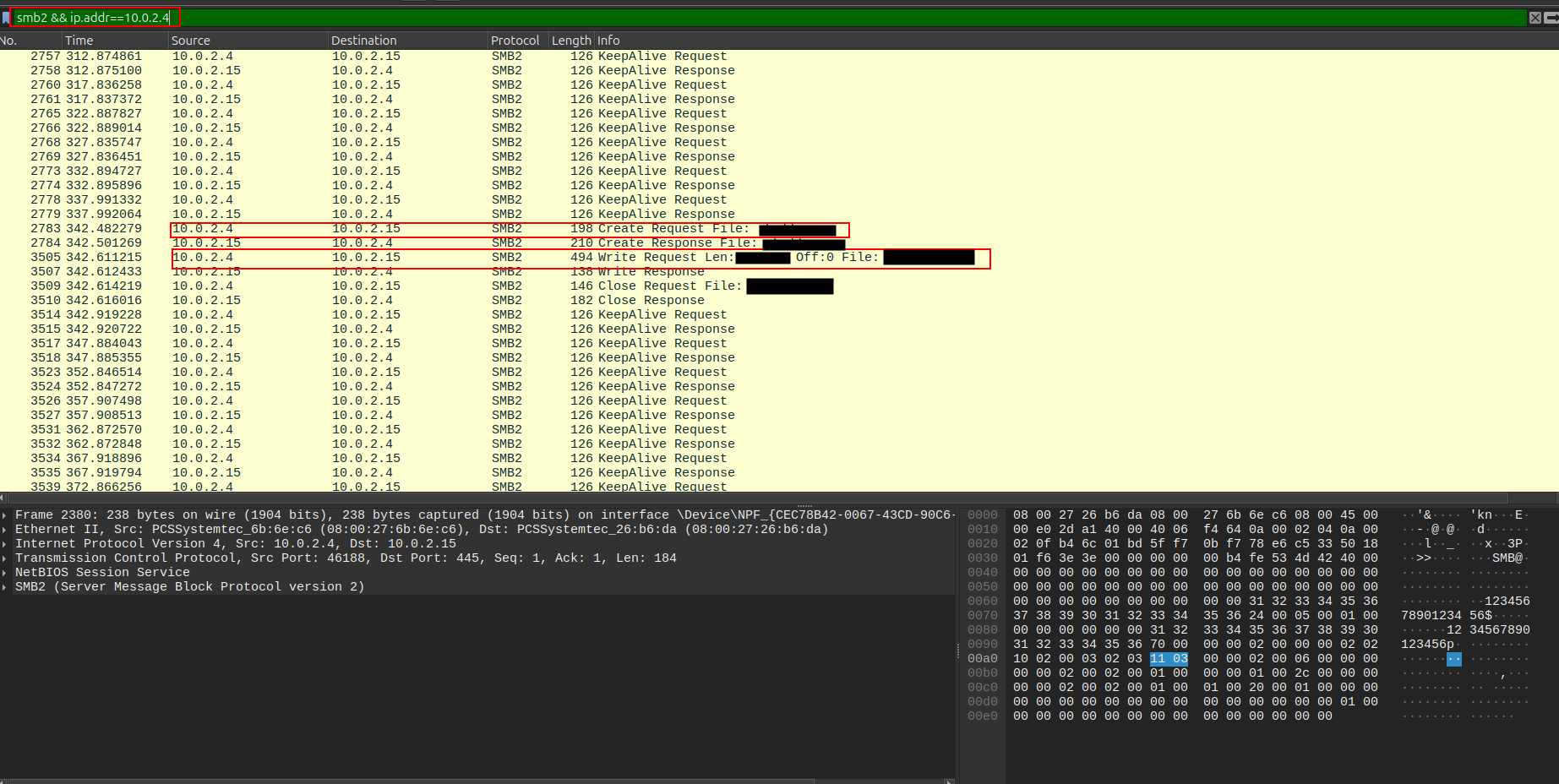
🔹 Q4 — Filename and SMB2 Write byte length
Using the same filter smb2 && ip.addr==10.0.2.4 nd scrolling through the SMB2 stream, I found a Create Request followed by a Write Request specifying both the filename and the payload size
🔹 Q5 — Reverse shell listening port
Analyzing TCP endpoints and conversations .
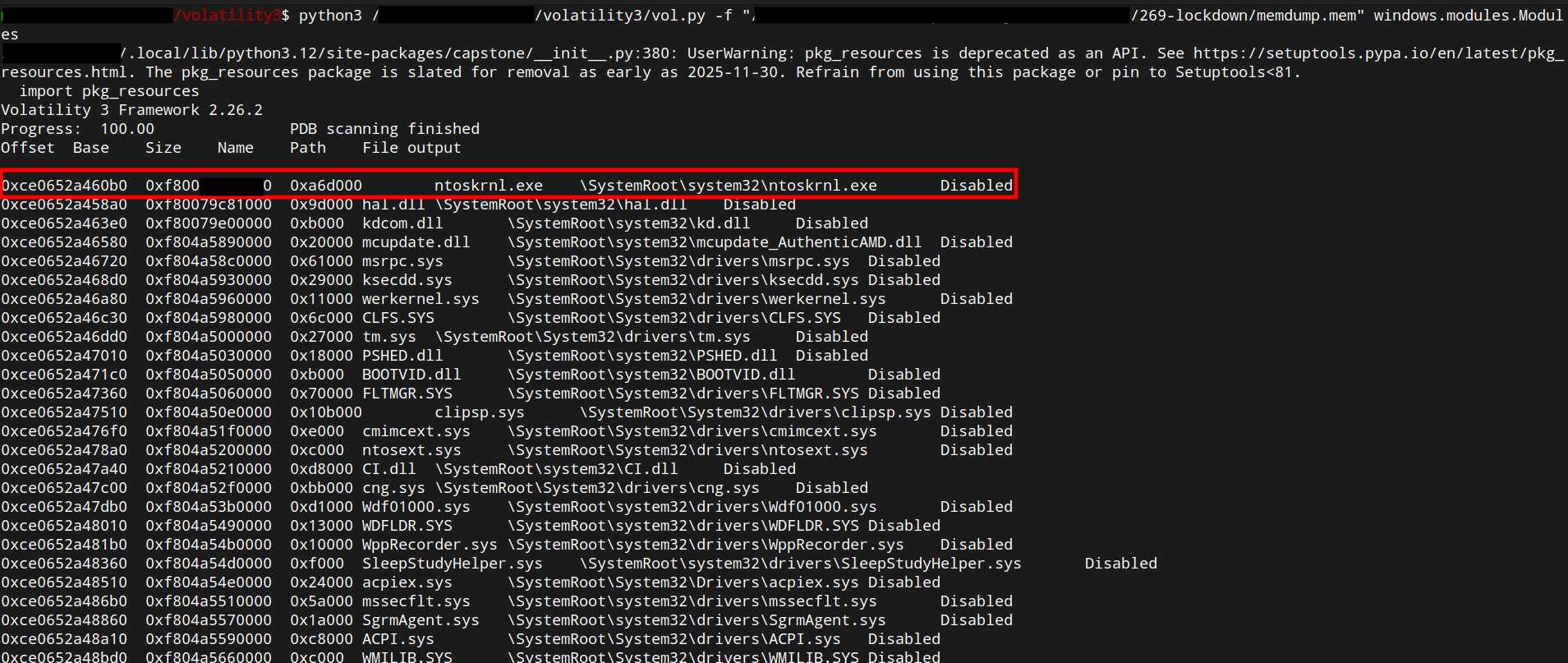
🔹 Q6 — What is the kernel base address ?
Using Volatility3 with the windows.modules.Modules plugin yields the kernel base address.
🔹 Q7 — Full on-disk path and MITRE persistence technique
Using Volatility3 with ` windows.pstree.PsTree` and searching for updatenow.exe reveals the implant’s on-disk location.
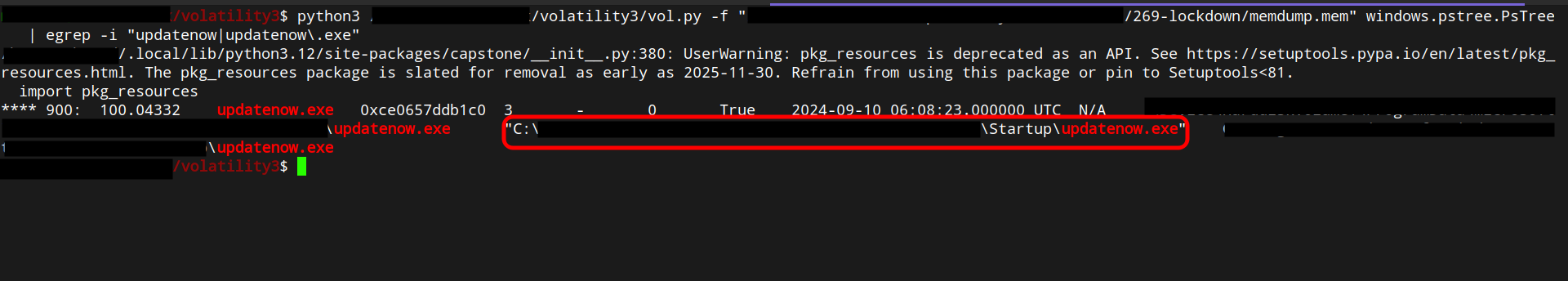
With the full path you will understand what Technique was used ( Autostarting )then you can search with that on MITRE website
🔹 Q8 — What is the name of this process, and what PID?
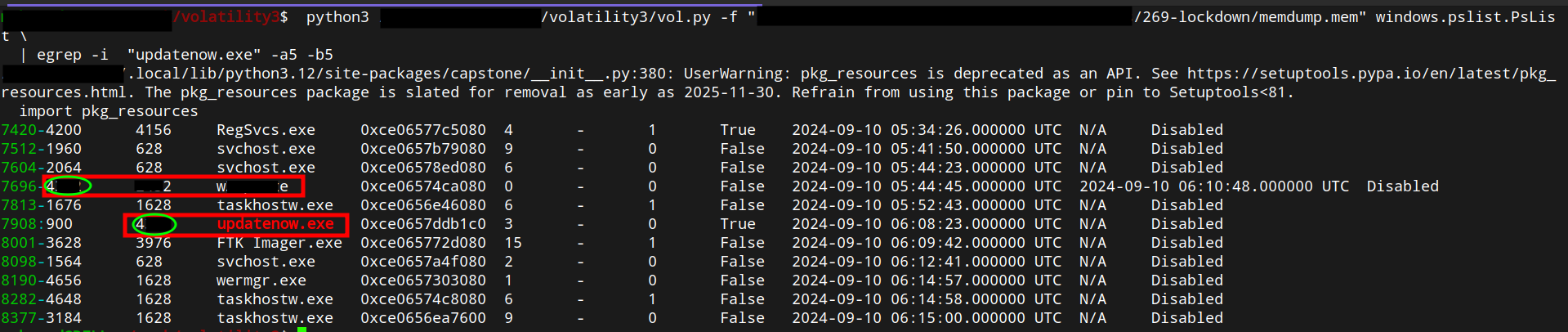
Using Volatility3 with windows.pslist.Pslistand searching for updatenow.exe
shows the process and PID. Cross-referencing the process tree confirms the built-in parent process that spawned the implant.
🔹 Q9 — Which packer was used to obfuscate it?
VirusTotal analysis indicated the binary was UPX compressed.
You can confirm with the file utility:
$ file updatenow.exe
updatenow.exe: PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections
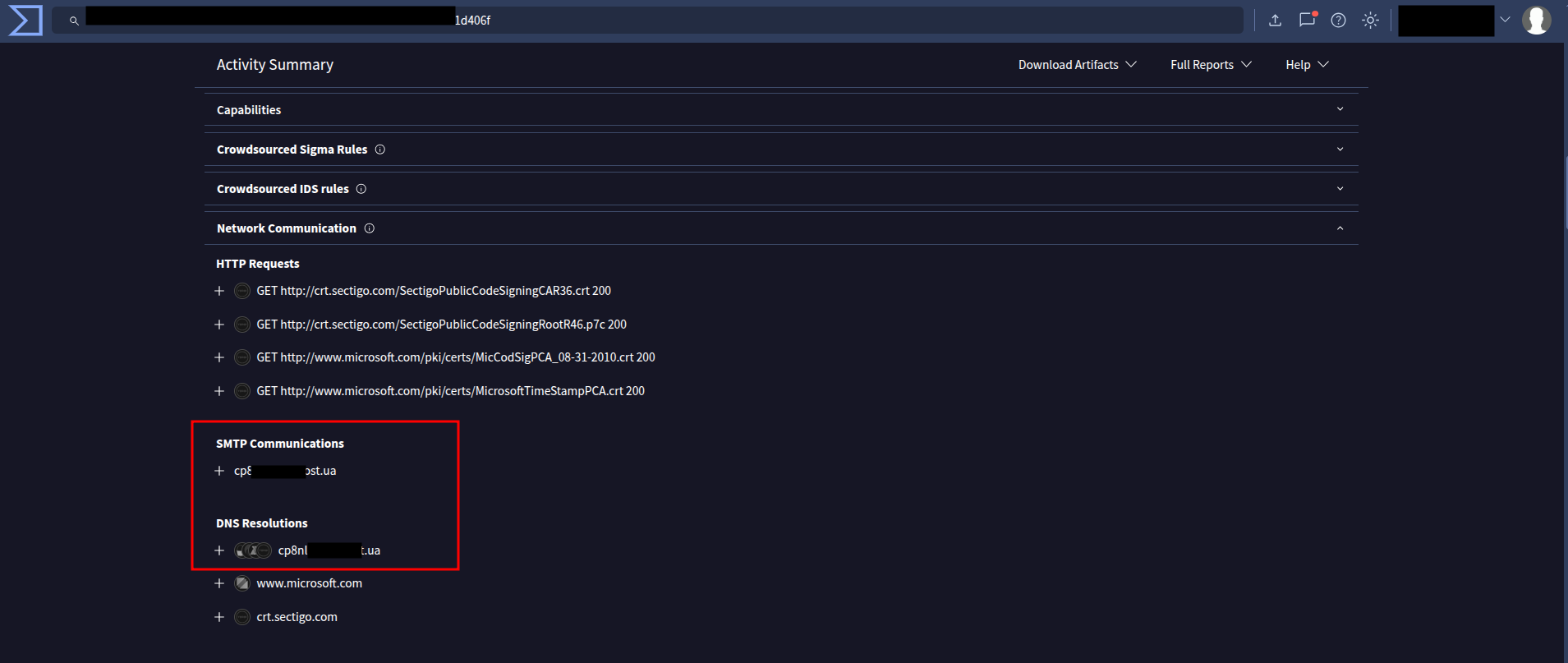
🔹 Q10 — Which fully qualified domain name (FQDN) does it contact?
The malware’s behavior report on VirusTotal and the DNS resolution entries reveal the C2 domain.
or you can run it on a sand box and inespect the ip traffic to get the anser
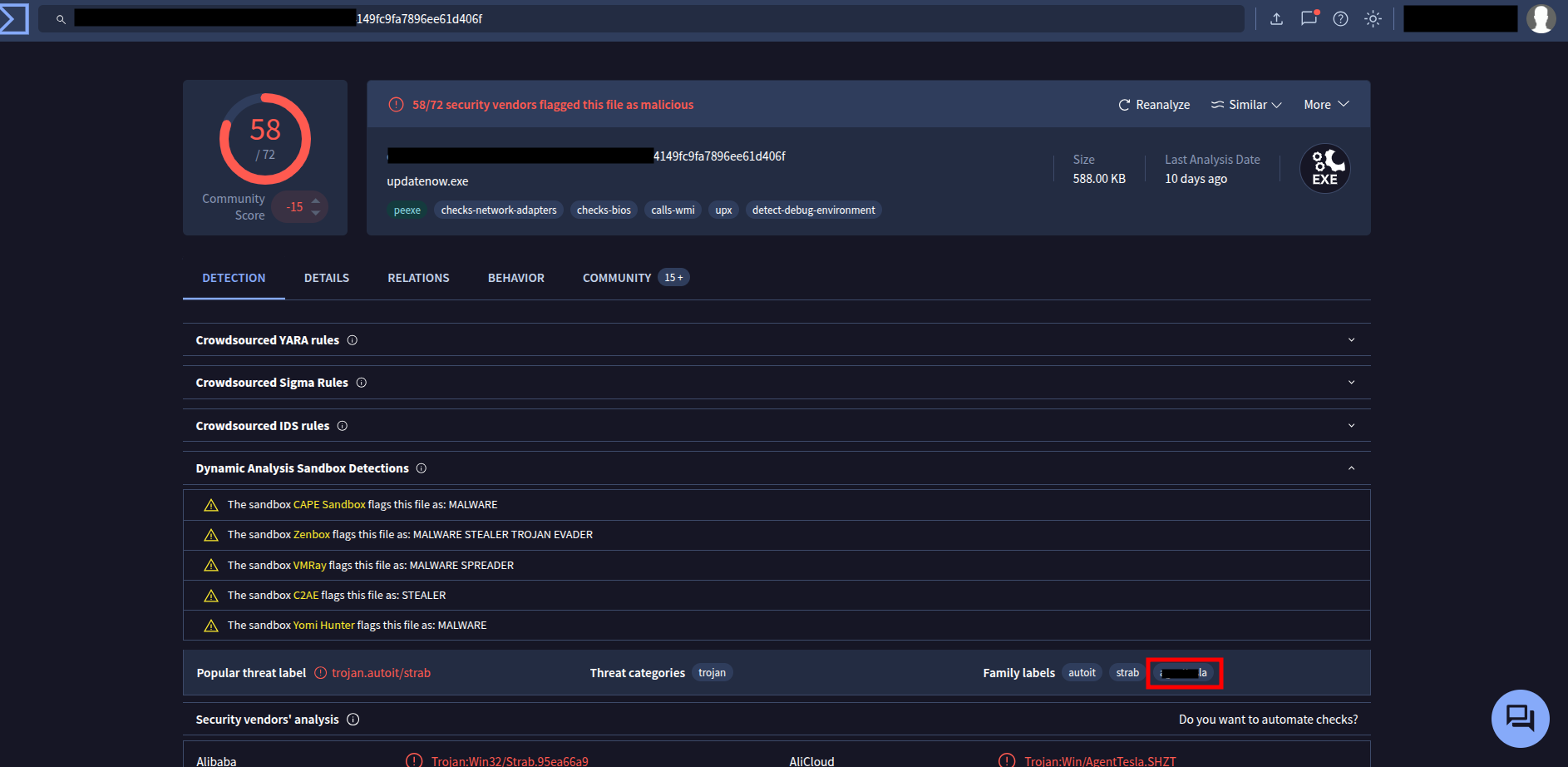
🔹 Q11 — To which malware family does the sample belong?
VirusTotal and community detectioned this hash with a known commodity RAT.
And that’s all for today’s write-up!
I hope you enjoyed it — see you in the next one! 👋🏻
اللهم انفعنا بما علَّمتنا، وعلِّمنا ما ينفعنا، وزِدنا علمًا وفقهًا وفهمًا